
版权所有 © 2021 ESET, spol. s r.o.
ESET PROTECT 由 ESET, spol. s r.o. 开发
有关更多信息,请访问 www.eset.com。
保留所有权利。未经作者书面同意,本文档的任何部分均不得复制、存入检索系统或以任何形式或任何方式传播,包括
电子的、机械的、影印、记录、扫描或其他方式。
ESET, spol. s r.o. 保留未经事先通知即更改任何所述应用程序软件的权利。
客户服务:www.eset.com/support
修订日期 2021年m月18日

1 介绍 1 ...................................................................................................................................................................
1.1 ESET Endpoint 产品 1 ..................................................................................................................................
1.2 ESET PROTECT 8.0 中的新功能 1 .................................................................................................................
2 ESET PROTECT 组件和体系结构 2 .........................................................................................................
3 系统要求 2 .........................................................................................................................................................
3.1 硬件 2 .............................................................................................................................................................
3.2 操作系统 3 ......................................................................................................................................................
3.3 网络 4 .............................................................................................................................................................
3.4 软件 5 .............................................................................................................................................................
4 安装 5 ...................................................................................................................................................................
4.1 ESET PROTECT 服务器的一体式安装 5 .........................................................................................................
4.2 安装后步骤 17 ................................................................................................................................................
5 ESET PROTECT 结构 18 ...............................................................................................................................
6 部署 20 .................................................................................................................................................................
6.1 部署程序包创建 20 .........................................................................................................................................
6.2 部署程序包安装 21 .........................................................................................................................................
6.3 其他部署方法 23 .............................................................................................................................................
6.4 ESET Remote Deployment Tool 23 ...........................................................................................................
7 后续步骤 26 .......................................................................................................................................................
7.1 面板 26 ...........................................................................................................................................................
7.2 计算机和组 27 ................................................................................................................................................
7.3 检测和隔离 28 ................................................................................................................................................
7.4 报告 29 ...........................................................................................................................................................
7.5 任务、通知、策略 30 ......................................................................................................................................
8 帮助和支持 31 ..................................................................................................................................................
9 最终用户许可协议 32 ...................................................................................................................................
10 隐私政策 35 .....................................................................................................................................................

1
介绍
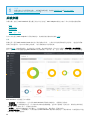
本指南旨在指导管理最多 250 台使用 ESET PROTECT 8 的 Windows ESET Endpoint 产品的中小型企业。
它将解释对于部署和使用 ESET 安全产品而言很重要的基本概念。
ESET PROTECT 8
ESET PROTECT 8(以前称为 ESMC)是一个应用程序,它允许您从一个中心位置管理网络环境中的客户端工作站、服务
器和移动设备上的 ESET 产品。 借助 ESET PROTECT 的内置任务管理系统,您可以在远程计算机上安装 ESET 安全解
决方案,并快速响应新的问题和威胁。
ESET PROTECT 本身不提供针对恶意代码的保护。 您的环境保护取决于工作站上是否存在 ESET 安全解决方案,例如
ESET Endpoint。
ESET Endpoint 产品
ESET Endpoint 产品主要设计用于小型商业/企业环境中的工作站,并且可以与 ESET PROTECT
结合使用。
ESET PROTECT 8
能够部署、激活或管理以下
ESET Endpoint
产品:
可通过以下产品管理 ESET PROTECT 8
产品版本
适用于 Windows 的 ESET Endpoint Security
6.5+, 7.x, 8.x
适用于 Windows 的 ESET Endpoint Antivirus
6.5+, 7.x, 8.x
适用于 macOS 的 ESET Endpoint Security
6.8+
适用于 macOS 的 ESET Endpoint Antivirus
6.8+
适用于 Android 的 ESET Endpoint Security
2.x
ESET PROTECT 8.0 中的新功能
重命名 ESET Security Management Center
ESET Security Management Center 将重命名为“ESET PROTECT”。 产品和服务不断发展,以满足新的市场和客户需求。
我们决定重命名我们的解决方案,以便更好地适配当前功能和我们计划的新功能。
ESET Full Disk Encryption 对于 macOS
我们计划扩展平台覆盖范围并添加 FileVault (适用于 macOS 的本地加密)管理,以提高组织的数据安全性。了解更多
高级功能
一些新功能侧重于满足大型网络的需求,以便可以进行更多自定义。这些功能都会并入现有用户界面中。
审核日志
新功能可帮助管理员识别和跟踪 ESET PROTECT 中的活动。轻松导航到运行任务、更改的策略、已解决的检测、添加的
用户或计算机,然后根据需要进行调整或更正。 了解更多
排除防火墙威胁
添加了从检测列表中排除防火墙威胁的功能。 了解更多
支持 ESET Business Account 站点
现在,可以导入 ESET Business Account 的完整结构,包括在站点之间分发许可证席位。

2
ESET PROTECT 组件和体系结构
若要执行 ESET 安全解决方案程序包的完整部署,必须安装以下组件:
• ESET PROTECT 服务器(控制与客户端计算机的通信)
• ESET PROTECT Web 控制台(适用于 ESET PROTECT 服务器的基于浏览器的用户界面)
• ESET Management 服务器代理(部署在客户端计算机上,与 ESET PROTECT 服务器通信)
虽然以下支持组件是可选的,但我们建议您安装它们,以在网络上实现应用程序的最佳性能:
• Apache HTTP 代理
• RD Sensor(可以检测网络上未托管的计算机)
服务器
ESET PROTECT 服务器(ESET PROTECT 服务器)是应用程序,用于处理从连接到服务器(通过 ESET Management 服
务器代理)的客户端接收的所有数据。
服务器代理
ESET Management 服务器代理是 ESET PROTECT8 的重要组成部分。客户端不会直接与服务器通信,而是借助服务器
代理实现此通信。服务器代理从客户端收集信息并将它发送到 ESET PROTECT 服务器。如果 ESET PROTECT 服务器发
送了一个客户端任务,该任务将发送到服务器代理,然后由服务器代理将它发送到客户端上运行的 ESET Endpoint 产品。
Web 控制台
ESET PROTECT Web 控制台是基于浏览器的用户界面,使您能够在自己的环境中管理 ESET 安全解决方案。 它将显示
您网络上的客户端状态的概述,并可用于将 ESET 解决方案远程部署到未托管的计算机。 如果您选择使 Web 服务器可
通过 Internet 进行访问,则几乎可以从任何地点和设备使用 ESET PROTECT。
Apache HTTP 代理
Apache HTTP 代理是可与 ESET PROTECT 8 结合使用的服务,用于将安装程序包和更新分发到客户端计算机。 它作为
透明代理使用,这意味着它会缓存已下载的文件,以最大程度减少您网络上的 Internet 流量。
使用 Apache HTTP 代理可提供以下优势
• 下载和缓存以下内容:
o检测引擎更新
o激活任务,包括与激活服务器通信和缓存许可证请求
oESET PROTECT 存储库数据
o产品组件更新 - Apache 代理可缓存更新并将它们分发到网络上的 Endpoint 客户端。
• 最大程度减少网络上的 Internet 流量。
Rogue Detection Sensor
Rogue Detection Sensor (RD Sensor) 在您的网络上搜索未在 ESET PROTECT 中注册的计算机。 此组件可以查找新的
计算机,然后自动将它们添加到 ESET PROTECT 中。
警告
Rogue Detection Sensor 可能需要最多 24 小时来查找您网络上的新计算机。
新发现的计算机会列在预定义报告中,从而方便将它们分配到特定的静态组并开始给它们分配任务。
系统要求
在安装 ESET PROTECT 之前,请验证所有硬件、操作系统、网络和软件先决条件都已得到满足。
硬件

3
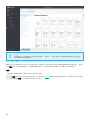
ESET PROTECT 服务器计算机应满足下表中的以下硬件建议。
SQL Server 实例可以与 ESET PROTECT 服务器共享资源,以实现利用率的最大化和延迟的最小化。在单台计算机上运
行 ESET PROTECT 服务器和数据库服务器可提高 ESET PROTECT 性能。
客户端数 ESET PROTECT 服务器 + SQL 数据库服务器
CPU 核心
RAM (GB)
磁盘驱动器
1
磁盘 IOPS
2
最多 1,000
4 4
单个
500
5,000 8 8 1.000
10,000
3
8 16
单独
2,000
50,000 16 32 10,000
100,000 16 32+ 20,000
磁盘驱动器建议
•
1
单个/单独磁盘驱动器:对于具有超过 10,000 个客户端的系统,建议您将数据库安装在单独的驱动器上。
o如果将数据库和事务日志文件放置在单独的驱动器上(最好是单独的物理 SSD 驱动器),则 SQL Server 的性能
将得到增强。
o将企业级 SSD 与高 IOPS f 或高性能系统结合使用。
• 2 IOPS(每秒 I/O 操作总数)- 最小要求值。
• 3 查看适用于 10,000 个客户端环境的示例方案。
• 建议每个连接的客户端的 IOPS 约为 0.2,但不小于 500。
• 可以使用 diskspd 工具的以下命令检查驱动器的 IOPS:
客户端数 命令
最多 5.000 个客户端
diskspd.exe -c1000M -b4K -d120 -Sh -r -z -w50 C:\testfile.dat
超过 5,000 个客户端
diskspd.exe -c10000M -b4K -d600 -Sh -r -z -w50 C:\testfile.dat
• 使用固态磁盘 (SSD),因为它们的速度比标准 HDD 快得多。
• 100 GB 容量足以满足任何数量的客户端。如果您经常备份数据库,可能需要更高的容量。
• 请勿使用网络驱动器,因为其性能会降低 ESET PROTECT 的速度。
重要信息
磁盘驱动器是影响 ESET PROTECT 性能的关键因素。
操作系统
下表显示了推荐用于中小型企业的各个 ESET PROTECT 组件支持的操作系统。 另请参阅受支持操作系统的完整列表。
操作系统 服务器 服务器代理
RD Sensor MDM
Windows Server 2008 R2 x64 SP1(已安装 KB4474419
或 KB4490628)
✔ ✔
Windows Server 2008 R2 CORE x64(已安装
KB4474419 或 KB4490628)
✔ ✔
Windows Server 2008 SP2(x86 和 x64,已安装
KB4493730 和 KB4039648)
✔ ✔
Windows Storage Server 2008 R2 x64(已安装
KB4474419 或 KB4490628)
✔ ✔
Windows Server 2012 x64 ✔ ✔ ✔ ✔
Windows Server 2012 CORE x64 ✔ ✔ ✔ ✔
Windows Server 2012 R2 x64 ✔ ✔ ✔ ✔
Windows Server 2012 R2 CORE x64 ✔ ✔ ✔ ✔
Windows Storage Server 2012 R2 x64 ✔ ✔ ✔ ✔

4
Windows Server 2016 x64 ✔ ✔ ✔ ✔
Windows Storage Server 2016 x64 ✔ ✔ ✔ ✔
Windows Server 2019 x64 ✔ ✔ ✔ ✔
Microsoft SBS 2008 x64 SP2(已安装 KB4493730 和
KB4039648)
✔ ✔ ✔
Microsoft SBS 2011 Standard x64 ✔ ✔ ✔ ✔
Microsoft SBS 2011 Essentials x64 ✔ ✔ ✔ ✔
操作系统 服务器 服务器代理
RD Sensor MDM
Windows 7 x86 SP1(已具有最新 Windows 更新,至少
KB4474419 和 KB4490628)
✔ ✔
Windows 7 x64 SP1(已具有最新 Windows 更新,至少
KB4474419 和 KB4490628)
✔ ✔
Windows 8 x86 ✔ ✔
Windows 8 x64 ✔* ✔ ✔ ✔*
Windows 8.1 x86 ✔ ✔
Windows 8.1 x64 ✔* ✔ ✔ ✔*
Windows 10 x86 ✔ ✔
Windows 10 x64(所有官方版本)
✔* ✔ ✔ ✔*
* 在客户端操作系统上安装 ESET PROTECT 组件可能违反 Microsoft 许可政策。检查 Microsoft 许可政策或者咨询您的
软件提供商以了解详细信息。 在 SMB/小型网络环境中,建议您使用 Linux ESET PROTECT 安装或虚拟设备(适用时)。
重要信息
• 旧版 MS Windows 系统:始终安装最新的服务包,尤其是在较旧的系统上,如 Server
2003、2008、Windows XP 和 Windows Vista。
• 我们不支持非法或盗版操作系统。
• 从 2020 年 3 月 24 日开始,ESET 将不再正式支持以下 Microsoft Windows 操作系统上安装的 ESET
PROTECT(Server 和 MDM)或为其提供技术支持:Windows 7、Windows Server 2008(所有版本)。
警告
从 2019 年 1 月开始,面向企业、商业或生产用途的 Oracle JAVA SE 8 公开更新将需要商业许可证。如
果不购买 JAVA SE 订阅,可以使用本指南来过渡到免费替代方案,并安装列出的受支持 Java 版本之一。
注意
可以在桌面操作系统上安装 VMware Player,并部署 ESET PROTECT 虚拟设备。这使您可以在非服务器
操作系统上运行 ESET PROTECT,而无需 ESXi。
网络
ESET PROTECT 服务器和 ESET PROTECT 管理的客户端计算机必须具有可以使用的 Internet 连接,才能够访问 ESET 存
储库和激活服务器。如果您不希望将客户端直接与 Internet 进行连接,可以使用代理服务器(与 Apache HTTP 代理不
同的代理服务器)来实现与您的网络和 Internet 进行通信。
ESET PROTECT 管理的计算机应连接到同一 LAN 和/或应位于与您的 ESET PROTECT 服务器相同的 Active Directory 域
中。 ESET PROTECT 服务器对于客户端计算机必须可见。 此外,客户端计算机必须能够与您的 ESET PROTECT 服务器

5
进行通信,才可以使用远程部署和唤醒呼叫功能。
使用的端口
如果您的网络使用防火墙,请参阅在基础结构中安装 ESET PROTECT 及其组件时所使用的可能网络通信端口列表。
软件
必须满足以下先决条件,才能在 Windows 上安装 ESET PROTECT 服务器:
• 必须具有有效的许可证。
• 必须安装 Microsoft .NET Framework 3.5;可以使用添加角色和功能向导安装它。
• ESET PROTECT Web 控制台需要 Java/OpenJDK(64 位)。
警告
从 2019 年 1 月开始,面向企业、商业或生产用途的 Oracle JAVA SE 8 公开更新将需要商业许可证。如
果不购买 JAVA SE 订阅,可以使用本指南来过渡到免费替代方案,并安装列出的受支持 Java 版本之一。
• ESET PROTECT 支持两种类型的数据库服务器,但建议您使用 ESET PROTECT 随附的 Microsoft SQL Server
Express 2019。
安装
ESET PROTECT 安装程序支持不同的格式,以便支持不同的安装方法。 我们建议针对小型部署使用一体式安装程序。
从以前版本的升级?
ESET PROTECT 服务器的一体式安装
ESET PROTECT 一体式安装程序仅适用于 Windows 操作系统。一体式安装程序允许您使用 ESET PROTECT 安装向导安
装所有 ESET PROTECT 组件。
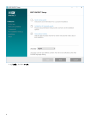
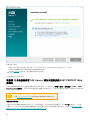
1. 打开安装包。在欢迎屏幕上,使用语言下拉菜单调整语言设置。单击下一步以继续。

6
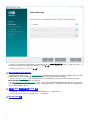
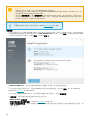
2. 选择安装,然后单击下一步。

7
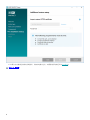
3. 如果您不同意将崩溃报告和遥测数据发送到 ESET,请取消选中参与产品改进计划复选框。如果选中该复选框,遥
测数据和崩溃报告将发送到 ESET。 接受 EULA 后,单击下一步。
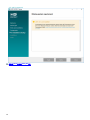
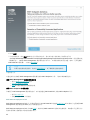
4. 选择要安装的适用组件,然后单击下一步。
Microsoft SQL Server Express
• ESET PROTECT 8.默认情况下,0 一体式安装程序将安装 Microsoft SQL Server Express 2019。如果使用的是旧版
Windows(Server 2012 或 SBS 2011),将默认安装 Microsoft SQL Server Express 2014。
• 如果已安装其他受支持版本的 Microsoft SQL Server 或 MySQL,或计划连接到其他 SQL Server,请取消选中
Microsoft SQL Server Express 旁边的复选框。
• 建议您在域控制器上不安装 SQL Server(例如,如果使用的是 Windows SBS/Essentials)。建议您在其他服务器上
安装 ESET PROTECT,或者在安装期间不选择 SQL Server Express 组件(这要求您使用现有 SQL 或 MySQL Server
来运行 ESET PROTECT 数据库)。
添加用于 Web 控制台的自定义 HTTPS 证书
• 如果要将自定义 HTTPS 证书用于 ESET PROTECT Web 控制台,请选择此选项。
• 如果不选择此选项,将自动为 Tomcat 生成一个新的密钥库。
Apache HTTP 代理

8
重要信息
Apache HTTP 代理选项仅适用于没有漫游客户端的小型或集中式网络。如果选择此选项,则客户端
将默认配置为通过与 ESET PROTECT 服务器安装在同一计算机上的代理与 ESET 进行隧道通信。如果
客户端和 ESET PROTECT 服务器之间没有直接的网络可见性,则此连接将不起作用。
• 使用 HTTP 代理可以大大节省用于从 Internet 下载数据的带宽,并提高产品更新的下载速度。建议您选中
Apache HTTP 代理旁边的复选框(如果将从 ESET PROTECT 管理 37 台以上计算机)。也可以选择稍后安装
Apache HTTP 代理。
• 有关详细信息,请参阅什么是 Apache HTTP 代理?和 Apache HTTP 代理、镜像工具和直接连接之间的区别。
• 选择 Apache HTTP 代理安装 Apache HTTP 代理,为以下产品创建并应用策略(名为 HTTP 代理使用,应用于
全部组):
oESET Endpoint for Windows
oESET Endpoint for macOS (OS X) and Linux
oESET Management Agent
oESET File Security for Windows Server (V6+)
oESET Shared Local Cache
该策略为受影响的产品启用 HTTP 代理。HTTP代理主机设置在 ESET PROTECT 服务器的本地 IP 地址和端口 3128 上。
身份验证已禁用。可以将这些设置复制到其他策略(如果需要设置其他产品)。
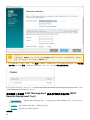
5. 如果已选择添加用于 Web 控制台的自定义 HTTPS 证书,则单击浏览并选择有效证书(.pfx 或 .p12 文件),然
后键入其密码(如果没有密码,将该字段留空)。该证书将安装在 Tomcat 服务器上,并用于 Web Console 访问。
单击下一步以继续。

11
注意
如果在系统上安装了多个版本的 Java,建议您卸载较旧版本的 Java(受支持的最旧版本是 Java 8),并
仅保留最新版本的 Java。
警告
从 2019 年 1 月开始,面向企业、商业或生产用途的 Oracle JAVA SE 8 公开更新将需要商业许可证。
如果不购买 JAVA SE 订阅,可以使用本指南来过渡到免费替代方案,并安装列出的受支持 Java 版本
之一。
a)要选择已安装的 Java,请单击选择 Java 安装,选择安装有 Java 的文件夹(包含子文件夹 bin,例如
C:\Program Files\Amazon Corretto\jdk1.8.0_212),然后单击确定。如果选择的路径无效,安装程序会提示您。
b)单击安装以继续,或单击更改以更改 Java 安装路径。
系统磁盘上仅 32 MB 可用
• 如果系统没有足够磁盘空间供 ESET PROTECT 安装,可能会显示此通知。
• 必须至少具有 4,400 MB 可用磁盘空间,才能安装 ESET PROTECT 及其所有组件。
ESET Remote Administrator 5.x 或较早版本安装在阻止安装程序继续的计算机上。
不支持直接升级 - 请参阅从 ERA 5.x 迁移。
7. 当先决条件检查完成并且环境满足所有要求时,将开始安装。请注意,安装可能需要一个小时以上,具体取决于
您的系统和网络配置。
注意
安装正在进行时,ESET PROTECT 安装向导不响应。

12
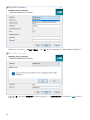
8. 如果在步骤 4 中选择安装 Microsoft SQL Server Express,则将执行数据库连接检查,且您应该跳到 Web
控制台用户和服务器连接。如果您具有现有数据库服务器,则在下一步中,系统将提示您输入数据库连接详细信息。
9. 如果使用现有的 SQL Server 或 MySQL,请相应地配置连接设置。将您的数据库名称、主机名、端口号(您可以在
Microsoft SQL Server 配置管理器中找到此信息)以及数据库帐户详细信息(用户名和密码)输入到相应字段中,然
后单击下一步。将验证与数据库的连接。如果您的数据库服务器上具有现有 ESET PROTECT 数据库(源自之前的
ERA/ESMC 安装),将检测到此情况。您可以选择使用现有的数据库并应用升级或删除现有的数据库并安装新版本。
使用命名实例 - 如果您使用的是 MS SQL 数据库,您还可以选择使用命名实例复选框。这将允许您使用自定义数据库
实例,例如您可以在 HOSTNAME\DB_INSTANCE 表的“主机名”字段中设置它:192.168.0.10\ESMC7SQL。对于群集
数据库,仅使用群集名称。如果选中此选项,则无法更改将使用哪个端口,系统将使用由 Microsoft 确定的默认端口。
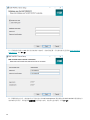
注意
选中使用命名实例复选框时,还可以将 ESET PROTECT 服务器连接到安装在故障转移群集中的 MS SQL
数据库。在主机名字段中,输入群集名称。
注意
输入数据库帐户信息时,有两个选项可供选择。您可以使用专用数据库用户帐户(将只具有 ESET
PROTECT 数据库的访问权限),也可以使用 SA 帐户 (MS SQL) 或根帐户 (MySQL)。如果您决定使用专用
用户帐户,需要创建具有特定权限的帐户。有关详细信息,请参阅专用数据库用户帐户。如果您不打算使
用专用用户帐户,请输入管理员帐户(SA 或根)。

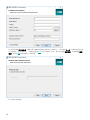
17
如果安装不成功:
• 查看一体式安装包中的安装日志文件。该日志所在目录与一体式安装程序的目录是同一个,例如:
C:\Users\Administrator\Downloads\x64\logs\
• 请参阅疑难解答以获取用于解决您的问题的其他步骤。
安装后步骤
在完成安装后,您应该可以:
连接到 已自动安装现有 SQL Server,我如何重新安装 ESET PROTECT Web
控制台
在本地 Windows 服务器(托管您的 Web 控制台的计算机)上,依次单击“开始”菜单 > 所有程序 > ESET > ESET
PROTECT Web 控制台 - 登录屏幕将在您的默认 Web 浏览器中打开。 如果显示 SSL 证书警告,请将该证书例外添加
到您的 Web 浏览器中。
重要信息
使用受支持的 Web 浏览器连接到 ESET PROTECT Web 控制台。
阅读启动向导说明
在您首次登录到 ESET PROTECT 控制台后,应该阅读说明,这会向您提供初步概述。 单击下一步以转到下一个屏幕。
在最后一步,可以开始为您的 ESET Endpoint 产品创建要向目标计算机部署的安装程序包。 您还可以稍后通过 ESET
PROTECT Web 控制台部署服务器代理和 ESET Endpoint 产品。
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
関連論文
-
ESET PROTECT 8.0 取扱説明書
-
ESET Endpoint Security for macOS 6.11 取扱説明書
-
ESET PROTECT 9.0—Guide 取扱説明書
-
ESET PROTECT 8.0 Installation/Upgrade Guide
-
ESET PROTECT 10.1—Guide 取扱説明書
-
ESET PROTECT 8.0 Installation/Upgrade Guide
-
ESET Endpoint Antivirus for macOS 6.11 取扱説明書
-
ESET Security Management Center 7.2 取扱説明書
-
ESET Security Management Center 7.2 取扱説明書
-
ESET Security Management Center 7.1 取扱説明書













































