
版权所有 © 2021 ESET, spol. s r.o.
ESET PROTECT Cloud 由 ESET, spol. s r.o. 开发
有关更多信息,请访问 www.eset.com。
保留所有权利。未经作者书面同意,本文档的任何部分均不得复制、存入检索系统或以任何形式或任何方式传播,包括
电子的、机械的、影印、记录、扫描或其他方式。
ESET, spol. s r.o. 保留未经事先通知即更改任何所述应用程序软件的权利。
客户服务:www.eset.com/support
修订日期 2021年m月22日

1 关于帮助 1 .........................................................................................................................................................
1.1 图标图例 1 ......................................................................................................................................................
2 释放注释 3 .........................................................................................................................................................
3 服务的可用性 10 .............................................................................................................................................
4 ESET PROTECT Cloud 简介 10 .................................................................................................................
4.1 ESET PROTECT Cloud 中的新功能 12 ..........................................................................................................
4.2 受支持的 Web 浏览器、ESET 安全产品和语言 13 ...........................................................................................
4.3 支持的操作系统 14 .........................................................................................................................................
4.4 先决条件 17 ....................................................................................................................................................
4.5 本地和云管理控制台之间的区别 17 .................................................................................................................
5 开始使用 ESET PROTECT Cloud 18 .......................................................................................................
5.1 使用 ESET Business Account 创建新的 ESET PROTECT Cloud 实例 19 ...................................................
5.2 在 ESET Business Account 中创建新的 ESET PROTECT Cloud 用户 21 ...................................................
5.3 ESET PROTECT Cloud Web 控制台 26 ........................................................................................................
5.3.1 登录屏幕 29 ..............................................................................................................................................
5.3.2 使用启动向导 30 ........................................................................................................................................
5.3.3 用户设置 33 ..............................................................................................................................................
5.3.4 过滤器和布局自定义 34 ................................................................................................................................
5.3.5 位号 37 ....................................................................................................................................................
5.3.6 导入 CSV 40 ..............................................................................................................................................
5.3.7 疑难解答 - Web 控制台 41 .............................................................................................................................
5.4 将 ESET PROTECT Cloud 与 Active Directory 同步 41 .............................................................................
5.5 如何在 ESET PROTECT Cloud 中管理 Endpoint 产品 45 ............................................................................
5.6 ESET 推送通知服务 45 ...................................................................................................................................
6 VDI、克隆和硬件检测 46 ...............................................................................................................................
6.1 解决克隆问题 48 .............................................................................................................................................
6.2 硬件标识 50 ....................................................................................................................................................
7 Apache HTTP 代理 50 ...................................................................................................................................
7.1 Apache HTTP 代理安装和缓存 51 .................................................................................................................
7.1.1 Squid 安装和 HTTP 代理缓存 53 .......................................................................................................................
7.2 Apache HTTP 代理安装 - Linux 54 ..............................................................................................................
7.2.1 Ubuntu Server 上的 Squid HTTP 代理安装 57 ......................................................................................................
8 ESET Management服务器代理部署 58 ................................................................................................
8.1 使用 RD Sensor 添加计算机 58 ....................................................................................................................
8.1.1 ESET Rogue Detection Sensor 策略设置 60 .........................................................................................................
8.1.2 RD Sensor 安装 60 .......................................................................................................................................
8.1.3 RD Sensor 先决条件 61 .................................................................................................................................
8.2 本地部署 61 ....................................................................................................................................................
8.2.1 创建服务器代理(和 ESET 安全产品)安装程序 61 ...............................................................................................
8.2.1.1 ESET PROTECT Live Installer 行为 63 ..............................................................................................................
8.2.2 服务器代理安装程序 Linux 63 ........................................................................................................................
8.2.2.1 部署服务器代理 - Linux 64 .........................................................................................................................
8.2.2.2 服务器代理先决条件 - Linux 64 ....................................................................................................................
8.2.3 服务器代理安装程序 (MacOS) 64 ....................................................................................................................
8.3 远程部署 65 ....................................................................................................................................................
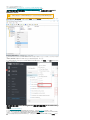
8.3.1 使用 GPO 和 SCCM 进行服务器代理部署 65 .......................................................................................................
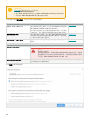
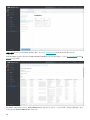
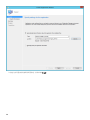
8.3.1.1 部署步骤 - SCCM 66 .................................................................................................................................
8.3.2 ESET Remote Deployment Tool 81 ...................................................................................................................
8.3.2.1 ESET 部署工具先决条件 82 ..........................................................................................................................
8.3.2.2 从 Active Directory 中选择计算机 82 .............................................................................................................
8.3.2.3 扫描本地网络以查找计算机 84 .....................................................................................................................
8.3.2.4 导入计算机列表 85 ...................................................................................................................................
8.3.2.5 手动添加计算机 87 ...................................................................................................................................

8.3.2.6 ESET Remote Deployment Tool - 故障排除 88 ...................................................................................................
8.4 服务器代理保护 90 .........................................................................................................................................
8.5 ESET Management 服务器代理设置 90 .......................................................................................................
8.5.1 创建策略以启用 ESET Management 服务器代理密码保护 91 ...................................................................................
8.6 疑难解答 - 服务器代理连接 92 ......................................................................................................................
9 ESET PROTECT Cloud 主菜单 93 ............................................................................................................
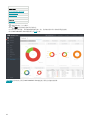
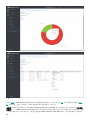
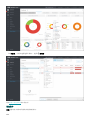
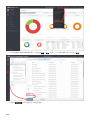
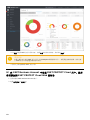
9.1 面板 93 ...........................................................................................................................................................
9.1.1 深入了解 95 ..............................................................................................................................................
9.2 计算机 96 .......................................................................................................................................................
9.2.1 计算机详细信息 97 ......................................................................................................................................
9.2.2 从管理中删除计算机 101 ..............................................................................................................................
9.2.3 组 102 ....................................................................................................................................................
9.2.3.1 组操作 103 ............................................................................................................................................
9.2.3.2 组详细信息 103 ......................................................................................................................................
9.2.3.3 静态组 104 ............................................................................................................................................
9.2.3.3.1 创建新静态组 105 .................................................................................................................................
9.2.3.3.2 导出静态组 106 ....................................................................................................................................
9.2.3.3.3 导入静态组 107 ....................................................................................................................................
9.2.3.4 动态组 108 ............................................................................................................................................
9.2.3.4.1 创建新动态组 109 .................................................................................................................................
9.2.3.5 移动静态或动态组 111 ..............................................................................................................................
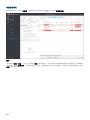
9.2.3.6 将客户端任务分配给组 112 ........................................................................................................................
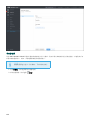
9.2.3.7 将策略分配到组 113 .................................................................................................................................
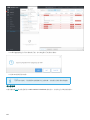
9.3 检测 114 .........................................................................................................................................................
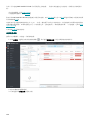
9.3.1 管理检测 116 ............................................................................................................................................
9.3.2 创建排除 116 ............................................................................................................................................
9.3.2.1 与排除兼容的 ESET 安全产品 118 ................................................................................................................
9.3.3 勒索软件防护 119 ......................................................................................................................................
9.4 报告 119 .........................................................................................................................................................
9.4.1 创建新报告模板 121 ....................................................................................................................................
9.4.2 生成报告 124 ............................................................................................................................................
9.4.3 计划报告 124 ............................................................................................................................................
9.4.4 过期的应用程序 125 ....................................................................................................................................
9.4.5 SysInspector 日志查看器 125 .........................................................................................................................
9.4.6 硬件清单 126 ............................................................................................................................................
9.4.7 审核日志报告 127 ......................................................................................................................................
9.5 任务 128 .........................................................................................................................................................
9.5.1 客户端任务 129 .........................................................................................................................................
9.5.1.1 客户端任务触发器 130 ..............................................................................................................................
9.5.1.1.1 将客户端任务分配给组或计算机 131 ..........................................................................................................
9.5.1.2 防盗操作 132 .........................................................................................................................................
9.5.1.3 诊断 134 ...............................................................................................................................................
9.5.1.4 显示消息 135 .........................................................................................................................................
9.5.1.5 结束计算机与网络隔离 136 ........................................................................................................................
9.5.1.6 导出托管产品配置 137 ..............................................................................................................................
9.5.1.7 将计算机与网络隔离 138 ...........................................................................................................................
9.5.1.8 模块更新 138 .........................................................................................................................................
9.5.1.9 模块更新回滚 139 ....................................................................................................................................
9.5.1.10 手动扫描 140 ........................................................................................................................................
9.5.1.11 操作系统更新 141 ..................................................................................................................................
9.5.1.12 隔离区管理 142 .....................................................................................................................................
9.5.1.13 产品激活 143 ........................................................................................................................................
9.5.1.14 重置克隆的代理 143 ...............................................................................................................................
9.5.1.15 Rogue Detection Sensor 数据库重置 144 .......................................................................................................
9.5.1.16 运行命令 145 ........................................................................................................................................
9.5.1.17 运行 SysInspector 脚本 146 ......................................................................................................................
9.5.1.18 服务器扫描 147 .....................................................................................................................................

9.5.1.19 关闭计算机 147 .....................................................................................................................................
9.5.1.20 软件安装 148 ........................................................................................................................................
9.5.1.20.1 升级 ESET 软件 150 .............................................................................................................................
9.5.1.20.2 Safetica 软件 151 .................................................................................................................................
9.5.1.21 软件卸载 151 ........................................................................................................................................
9.5.1.22 停止管理(卸载 ESET Management 服务器代理) 152 .....................................................................................
9.5.1.23 SysInspector 日志请求(仅限 Windows) 153 ....................................................................................................
9.5.1.24 升级服务器代理 154 ...............................................................................................................................
9.5.1.25 上载隔离的文件 155 ...............................................................................................................................
9.5.2 服务器任务 156 .........................................................................................................................................
9.5.2.1 删除未连接的计算机 156 ...........................................................................................................................
9.5.2.2 生成报告 157 .........................................................................................................................................
9.5.2.3 重命名计算机 158 ....................................................................................................................................
9.5.3 任务触发器类型 159 ....................................................................................................................................
9.5.3.1 CRON 表达式间隔 160 ................................................................................................................................
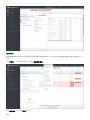
9.5.4 高级设置 - 限制 162 ..................................................................................................................................
9.5.4.1 限制示例 165 .........................................................................................................................................
9.5.5 任务概述 167 ............................................................................................................................................
9.5.5.1 进度指示器 168 ......................................................................................................................................
9.5.5.2 状态图标 168 .........................................................................................................................................
9.5.5.3 任务详细信息 169 ....................................................................................................................................
9.6 安装程序 171 ..................................................................................................................................................
9.7 策略 173 .........................................................................................................................................................
9.7.1 策略向导 174 ............................................................................................................................................
9.7.2 标志 175 ..................................................................................................................................................
9.7.3 管理策略 176 ............................................................................................................................................
9.7.4 如何将策略应用到客户端 176 ........................................................................................................................
9.7.4.1 对组进行排序 177 ....................................................................................................................................
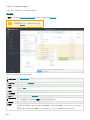
9.7.4.2 枚举策略 178 .........................................................................................................................................
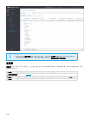
9.7.4.3 合并策略 179 .........................................................................................................................................
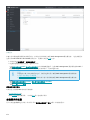
9.7.4.3.1 合并策略的示例方案 180 ........................................................................................................................
9.7.5 从 ESET PROTECT Cloud 配置产品 183 .............................................................................................................
9.7.6 将策略分配到组 183 ....................................................................................................................................
9.7.7 将策略分配给客户端 184 ..............................................................................................................................
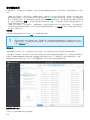
9.7.8 如何使用覆盖模式 185 .................................................................................................................................
9.8 通知 187 .........................................................................................................................................................
9.8.1 管理通知 188 ............................................................................................................................................
9.8.1.1 托管计算机上的事件 188 ...........................................................................................................................
9.8.1.2 ESET PROTECT Cloud 的状态更新 189 ............................................................................................................
9.8.1.3 动态组更改 190 ......................................................................................................................................
9.8.2 分发 190 ..................................................................................................................................................
9.9 状态概述 191 ..................................................................................................................................................
9.10 更多 192 .......................................................................................................................................................
9.10.1 提交的文件 192 ........................................................................................................................................
9.10.2 排除 193 ................................................................................................................................................
9.10.3 隔离 196 ................................................................................................................................................
9.10.4 计算机用户 197 ........................................................................................................................................
9.10.4.1 添加新用户 197 .....................................................................................................................................
9.10.4.2 编辑用户 199 ........................................................................................................................................
9.10.4.3 创建新用户组 200 ..................................................................................................................................
9.10.5 动态组模板 201 ........................................................................................................................................
9.10.5.1 新建动态组模板 202 ...............................................................................................................................
9.10.5.2 动态组模板的规则 203 .............................................................................................................................
9.10.5.2.1 操作 203 ...........................................................................................................................................
9.10.5.2.2 规则和逻辑连接符 203 ..........................................................................................................................
9.10.5.2.3 模板规则评估 204 ...............................................................................................................................
9.10.5.3 动态组模板 - 示例 206 ...........................................................................................................................
9.10.5.3.1 动态组 - 已安装安全产品 206 ................................................................................................................

9.10.5.3.2 动态组 - 已安装特定软件版本 207 ..........................................................................................................
9.10.5.3.3 动态组 - 未安装特定版本的软件 207 ........................................................................................................
9.10.5.3.4 动态组 - 未安装特定版本的软件,但存在其他版本 207 .................................................................................
9.10.5.3.5 动态组 - 计算机位于特定子网中 208 ........................................................................................................
9.10.5.3.6 动态组 - 已安装但未激活服务器安全产品的版本 208 ....................................................................................
9.10.5.4 如何自动化 ESET PROTECT Cloud 208 .........................................................................................................
9.10.6 许可证管理 209 ........................................................................................................................................
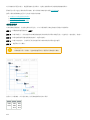
9.10.7 访问权限 212 ...........................................................................................................................................
9.10.7.1 用户 213 .............................................................................................................................................
9.10.7.1.1 用户操作和用户详细信息 215 .................................................................................................................
9.10.7.1.2 将权限集分配给用户 216 .......................................................................................................................
9.10.7.1.3 双因素身份验证 217 .............................................................................................................................
9.10.7.2 权限集 218 ...........................................................................................................................................
9.10.7.2.1 管理权限集 220 ..................................................................................................................................
9.10.7.2.2 权限列表 221 .....................................................................................................................................
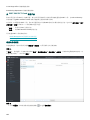
9.10.8 审核日志 224 ...........................................................................................................................................
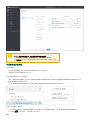
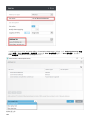
9.10.9 设置 225 ................................................................................................................................................
9.10.9.1 系统日志安全限制和限制 228 ....................................................................................................................
9.10.10 将日志导出到系统日志 228 ........................................................................................................................
9.10.10.1 系统日志服务器 229 ..............................................................................................................................
9.10.10.2 导出为 LEEF 格式的事件 229 ....................................................................................................................
9.10.10.3 导出为 JSON 格式的事件 229 ...................................................................................................................
10 适用于托管服务提供商的 ESET PROTECT Cloud 231 ................................................................
10.1 适用于 MSP 用户的 ESET PROTECT Cloud 的功能 233 .............................................................................
10.2 在 ESET MSP Administrator 中创建新的 ESET PROTECT Cloud 用户 234 .............................................
10.3 MSP 的部署过程 236 ...................................................................................................................................
10.3.1 服务器代理的本地部署 237 ..........................................................................................................................
10.3.2 服务器代理的远程部署 237 ..........................................................................................................................
10.4 MSP 许可证 237 ..........................................................................................................................................
10.5 开始 MSP 客户设置 239 ...............................................................................................................................
10.6 跳过 MSP 客户设置 242 ...............................................................................................................................
10.7 创建自定义安装程序 242 ..............................................................................................................................
10.8 MSP 用户 245 ..............................................................................................................................................
10.9 标记 MSP 对象 247 ......................................................................................................................................
10.10 MSP 状态概述 247 .....................................................................................................................................
10.11 删除公司 249 ..............................................................................................................................................
11 云移动设备管理 250 ....................................................................................................................................
11.1 CMDM 注册 251 ..........................................................................................................................................
11.2 CMDM 管理 252 ..........................................................................................................................................
12 ESET PROTECT Cloud 迁移方案 252 ...................................................................................................
12.1 从 ESMC 7/ESET PROTECT 8 部分迁移到 ESET PROTECT Cloud 253 .....................................................
13 停止使用 ESET PROTECT Cloud 267 ..................................................................................................
13.1 最后的 ESET PROTECT Cloud 许可证到期 268 ..........................................................................................
14 关于 ESET PROTECT Cloud 269 ............................................................................................................
15 ESET PROTECT Cloud 安全 269 ............................................................................................................
16 使用条款 273 ...................................................................................................................................................
16.1 ESET Management 服务器代理最终用户许可协议 275 ..............................................................................
16.2 数据处理协议 278 .........................................................................................................................................
16.3 标准合同条款 279 .........................................................................................................................................
17 隐私政策 283 ...................................................................................................................................................
18 云合格许可证 284 .........................................................................................................................................

19 预览功能 285 ...................................................................................................................................................
19.1 iOS 管理 287 ................................................................................................................................................
19.2 计算机预览 287 ............................................................................................................................................

1
关于帮助
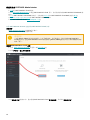
编写《管理指南》的目的是帮助您熟悉 ESET PROTECT Cloud 并提供使用说明。
为了保持一致和帮助避免混淆,本指南中使用的术语均基于 ESET PROTECT Cloud 参数名称。我们还使用了一组符号来
突出显示特定关注内容或重要内容的主题。
注意
注释可以提供有价值的信息,例如特定功能或指向某些相关主题的链接。
重要信息
这些信息需要您注意,请勿跳过。它通常提供并非关键但很重要的信息。
警告
您应格外注意的关键信息。警告专门用于防止您犯潜在有害的错误。请阅读并了解警告括号中包含的文本,
因为它引用了高度敏感的系统设置或有风险的内容。
示例
示例方案描述与其所属主题相关的用例。示例用于解释更复杂的主题。
约定 含义
粗体类型 界面项目的名称,例如框和选项按钮。
斜体类型
您提供的信息的占位符。例如,文件名称或路径表示您键入实际路径或文件名称。
宋体 代码示例或命令
超链接 支持快速轻松地访问交叉引用的主题或外部 Web 位置。超链接以蓝色突出显示,可能带有下划线。
%ProgramFiles%
可存储 Windows 已安装程序和其他程序的 Windows 系统目录。
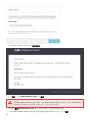
• 联机帮助是帮助内容的主要来源。当您有正常的 Internet 连接时,将自动显示联机帮助的最新版本。
• 本指南中的主题分为几个章节和子章节。您可以通过使用顶部的搜索字段来查找相关信息。
• ESET 知识库包含对最常见问题的解答以及各种问题的建议解决方案。知识库由 ESET 专业技术人员定期更新,它
已成为解决各类问题的最强大工具。
• ESET 论坛可使 ESET 用户轻松获取帮助,并为他人提供帮助。您可以发布任何与您的 ESET 产品相关的问题或难
题。
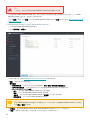
图标图例
这是整个 ESET PROTECT Cloud Web 控制台中所使用的图标集合,带有相应说明。有些图标描绘操作、项目类型或当
前状态。大多数图标显示为以下三种颜色之一,以表示元素的可访问性:
默认图标 - 可用操作
蓝色图标 - 使用鼠标指针悬停时突出显示的元素
灰色图标 - 操作不可用
状
态
图
标
说明
显示详细信息 - 有关客户端设备的详细信息。

2
状
态
图
标
说明
新增 - 添加新设备。
新任务 - 添加新任务。
新通知 - 添加新通知。
新静态/动态组 - 添加新组
编辑 - 可以编辑已创建的任务、通知、报告模板、组、策略等。
复制 - 允许您根据所选的现有策略创建新策略,复制需要一个新名称。
移动 - 计算机、策略、静态组或动态组。
访问组 - 将项目移动到不同的静态组。
删除 - 完全删除选定的客户端、组等。
重命名多个项目 - 如果选择多个项目,可逐个重命名列表中的项目,或者使用“正则表达式”同时搜索和替换多
个项目。
扫描 - 使用此选项将在报告了检测的客户端上运行手动扫描任务。
更新模块 - 使用此选项将运行模块更新任务(手动触发更新)。
审核日志 - 查看选定项目的审核日志。
重新启动 – 如果选择一台计算机并按重新启动,该设备将重新启动。
恢复 - 将隔离文件恢复到其原始位置。
关机 - 如果选择一台计算机并单击重新启动 > 关机,该设备将关机。
停用产品
运行任务 - 选择一项任务,并为这项任务配置触发器和限制(可选)。该任务将根据任务设置进行排队。此选项
会立即触发从可用任务的列表中选择的现有任务。
上次使用的任务 - 显示上次使用的任务。可单击该任务,重新执行。
分配用户 - 将用户分配到设备。可在计算机用户中管理用户。
管理策略 - 还可以将策略直接分配到一个客户端(多个客户端),而不仅限于某个组。选择此选项以将策略分配
到选定的一个或多个客户端。
发送唤醒呼叫 - ESET PROTECT Cloud 服务器将通过 EPNS 在客户端计算机上运行 ESET Management 服务器代
理的即时复制。当 ESET Management 服务器代理连接到 ESET PROTECT Cloud 服务器时,如果您不想等待常规
间隔,这将非常有用。例如,在您希望客户端任务立即在客户端上运行,或者希望立即应用策略时。
与网络隔离
结束网络隔离
连接 – 生成并下载支持通过远程桌面协议连接到目标设备的 .rdp 文件。

3
状
态
图
标
说明
静音 - 如果您选择了一台计算机并按静音,此客户端上的服务器代理将停止向 ESET PROTECT Cloud 报告;它将
只汇总信息。静音图标 将显示在“已静音”列中计算机名称的旁边。
通过单击取消静音禁用静音后,已静音的计算机将重新报告,并且恢复 ESET PROTECT Cloud 与该客户端之间的
通信。
禁用 - 禁用或删除设置或选择。
分配 - 将策略分配到客户端或组。
导入 - 选择要导入的报告/策略。
导出 - 选择要导出的报告/策略。
位号 - 编辑标记(分配、取消分配、创建、删除)。
静态组
动态组
不应用策略标记
应用策略标记
强制执行策略标记
触发器 - 查看选定客户端任务的触发器列表。
桌面
服务器
文件服务器
邮件服务器
网关服务器
协作服务器
服务器代理
Rogue Detection Sensor
ESET Full Disk Encryption
启用 EDTD - 激活并启用 ESET Dynamic Threat Defense。
释放注释
ESET PROTECT Cloud 2.1.0
• ADDED: Ability to look up specific computer based on the last logged user parameter
• ADDED: Support for policy-based migration from on-premise console to cloud console
• FIXED: Issue with opening/reading PDF reports sent by email (base64-encoded)
• FIXED: Non-root user with write permission rights for ESET PROTECT Cloud in ESET Business Account cannot
import or create dynamic group templates
• FIXED: Device filters on Dashboards display different values than in tables
• FIXED: In some cases, Detail in the "Audit Log" overlapping other lines
• FIXED: Product deactivation fails with timeout (in certain cases) if started by "Delete not connected computers"

4
server task
• FIXED: User cannot delete objects in some cases even with correct access rights
• FIXED: Name of the file is garbled when Japanese characters are used
• FIXED: Various other bug fixes and minor improvements
ESET PROTECT Cloud 2.0.148.0
• CHANGED: ESET Cloud Administrator renamed to ESET PROTECT Cloud
• ADDED: Ability to manage and protect Android mobile devices
• ADDED: Ability to manage FileVault (macOS) native encryption when an eligible license is present
• ADDED: Increased device management limit (up to 10,000 - dependent on purchased license size)
• ADDED: One-click deployment of ESET Dynamic Threat Defense if an eligible license is present
• ADDED: Ability to manage dynamic groups
• ADDED: Ability to manage notifications
• ADDED: Ability to define specific permission sets for selected users
• ADDED: Active Directory synchronization (Computers only)
• ADDED: Syslog log exporting
• ADDED: New “Audit log” section provides detailed information about specific actions
• ADDED: Ability to mass deploy the management agent to macOS devices
• ADDED: Second-level menu for advanced options
• ADDED: Secure Browser management
• ADDED: Support for sites (ESET Business Account) licenses including new "License user" column
• ADDED: Renew a license in the “License Management” screen
• ADDED: Ability to drill-down from expiring license issues in “Dashboards” and “Reports” to obtain more
information in the “License Management” screen
• ADDED: New “Manage license” context menu
• ADDED: EULA update notifications that support auto-upgrade (uPCU) of endpoint products in managed
environments
• ADDED: New ESET Full Disk Encryption (EFDE) management actions directly from “Computer details”
• ADDED: New EFDE Dynamic groups and Reports
• ADDED: Detection details (LiveGrid, Observed in organization, Virus Total )
• ADDED: One-click access to client task triggers
• ADDED: Unsupported browser warning
• ADDED: New "Seats allocated to sites" present in dedicated license report
• ADDED: Multi-line command scripts for Run Command task
• ADDED: Option to create a Computer user group in the “Add computer user” wizard
• CHANGED: Management Agent - supported operating systems

5
• CHANGED: Retention policy defaults
• CHANGED: License unit/sub-units visualization changed to "used/total" for online licenses and "X offline" for
offline licenses
• CHANGED: Access to behavior reports (when EDTD is purchased and enabled) are available (in the UI) only if
an eligible license is present
• IMPROVED: Ability to define a retention policy for certain logs
• IMPROVED: Exclusions mechanism extended to firewall threats
• IMPROVED: Computer details now directly accessible by clicking the computer name
• IMPROVED: One-click Network isolation
• IMPROVED: Columns ordering
• IMPROVED: Pop-up with search option
• IMPROVED: Hierarchical Dynamic groups tree
• IMPROVED: Multi-select in pop-up (modal) windows
• IMPROVED: Ability to create one exclusion from multiple detentions with standard exclusion criteria(s)
• IMPROVED: Breadcrumbs for better navigation in Wizards
• IMPROVED: Various other performance and security improvements
• FIXED: “Delete task action” removes all client tasks, not just selected items in a task list for a specific group
• FIXED: Status filter not visible for server tasks (only in client tasks)
• FIXED: Failed to send a wake-up call from the client task details executions
• FIXED: Incorrect target group type displays when editing a client trigger
• FIXED: “Status update” type notifications fail to save if they contain the “$” character
• FIXED: Import of policies with large file sizes
• FIXED: Infinite units or subunits in tooltips for licenses in the License Management screen display incorrectly
• FIXED: License-related notifications (for example, expiration/overuse) trigger when a license is suspended
• FIXED: Policy does not block the selected Scan profile
• FIXED: Filters previously set are not saved
• FIXED: Various other bug fixes
ESET Cloud Administrator 1.2.118.0
• ADDED: Support for ESET Dynamic Thread Defense (Sold separately. Available for purchase in upcoming
weeks)
• ADDED: Submitted files screen
• ADDED: Ability to pause ESET Full Disk Encryption available from EFDE client version 1.2 (EFDE - purchased
separately)
• ADDED: Automatic resolution of firewall logs and filtered websites
• ADDED: Ukrainian language
• ADDED: New filtering options

6
• ADDED: Many other performance, usability, and security improvements
• IMPROVED: Discontinued the default limit for the number of displayed static groups
• IMPROVED: Performance improvements in the “groups” tree on the “Computers” and “Detections” screens
• IMPROVED: Selected screens redesign: Users, scheduled reports and edit updates in the navigation bar
• IMPROVED: Unified table design for task selection, computers selection, and other features
• IMPROVED: Second-level menu added under "Change assignments" in the policy screen
• FIXED: Delay of product version status shown in the main web console
• FIXED: System applications are not reported on macOS 10.15
• FIXED: Language detection on macOS Catalina
• FIXED: Table sorting behavior: Clicking column headers adds columns to multi-sorting until it has been clicked
3 times
• FIXED: Last scan time in “computer details” screen won’t impact the computer security status tile
• FIXED: User cannot resolve detections when the “Resolved” column is not shown in the “detections” table
• FIXED: The side panel does not remember the expanded/collapsed state after log-out and log-in
• FIXED: Some threats cannot be marked as resolved
• FIXED: After moving computers from a specific group, the view is changed to the group "ALL."
ESET Cloud Administrator - ESET Management Agent release- June
• ADDED: New version of ESET Management Agent
• ADDED: Updating ESET Management Agent to the latest version can be deployed centrally alongside the cloud
service update
• ADDED: Agent compatibility with H1/2021 Windows version 10
ESET Cloud Administrator 1.2.82.0
• IMPROVED: Email domain validation when sending live installer link was discontinued
• IMPROVED: Checkbox "automatically reboot when needed" not checked by default when activating EFDE from
encryption tile
• IMPROVED: Dozens of usability, security, performance and stability improvements
• FIXED: Clicking column headers adds columns to multi-sorting until it has been clicked 3 times
• FIXED: Last Scan Time should note trigger red security status
• FIXED: Not possible to resolve detections when "Resolution" column is not shown
• FIXED: The side panel doesn't remember expanded/collapsed state after log-out and log-in
• FIXED: Agents stop connecting to cloud service under some circumstances
• FIXED: Recipients not visible in notifications emails
• FIXED: Computer with outdated OS are not visible in appropriate dynamic group
• FIXED: Ability to create hash exclusion without a hash present
• FIXED: ESET Full Disk Encryption not included within the selective export task configuration

7
ESET Cloud Administrator 1.2
• NEW: ESET Full Disk Encryption
• NEW: Tagging - mark all relevant objects (e.g., computers) using user-defined tags
• NEW: Support for the newest generation of Linux products, starting with ESET File Security for Linux v7
• NEW: Centralized Exclusions and wizard
• ADDED: Option to automatically delete computers that are not connecting
• ADDED: Option to rename computers based on defined criteria
• ADDED: Computer isolation task
• ADDED: Unified table design with new navigation elements
• ADDED: Ability to export tables across all the main screens to different formats
• ADDED: New "empty screen states" for simpler object creation
• ADDED: Detections view is now aggregated by time and other criteria to simplify operations and to resolve
them
• ADDED: Execute one click actions from the "task executions" screen
• ADDED: Create a combined installer including ESET Full Disk Encryption
• ADDED: Option to deactivate individual products
• ADDED: New dynamic groups related to newly introduced products
• ADDED: Search by group name in computer screens and search bar
• ADDED: Option to save dashboard layout as preset for other users
• ADDED: Generate defined reports filtered to a selected group
• ADDED: Indonesian language support
• ADDED: New ESET Management Agent version (Windows) supports the latest security products
• IMPROVED: Many UI Improvements & other usability changes
• IMPROVED: Context menu now applies for all selected rows
• IMPROVED: Filtering panel has many new options such as autocomplete
• IMPROVED: New column selector element for primary tables.
• IMPROVED: Layout of detections (previously "threats") screen with new detection details
• IMPROVED: Reports screen layout includes a one click report generation option
• IMPROVED: Task section was updated and triggers are now displayed in a separate view of "task details"
• IMPROVED: Layout of policies screen, with simpler orientation and navigation
• IMPROVED: Layout of notifications screen with notification details
• IMPROVED: Quick links menu
• IMPROVED: AV remover (part of management agent) supports auto update
• IMPROVED: Download speeds from the repositories were significantly improved
• IMPROVED: Management agent file size significantly reduced

8
• CHANGED: "Threats" section was renamed to "Detections"
• CHANGED: Management agent compatibility update related to macOS 10.7 and 10.8 support (see the
documentation for more details)
• CHANGED: ESET Cloud Administrator ends support for Endpoint and Server Security versions 6.4 and earlier.
• FIXED: Various other bug fixes and internal performance improvements
ESET Cloud Administrator 1.1.360.0
• Added: Full support for endpoint version 7.1 products
• Fixed: Various bugs
ESET Cloud Administrator 1.1.359.0
• Improved: Internal performance improvements
ESET Cloud Administrator 1.1.358.0
• Improved: Overall performance improvements
• Changed: Updated copyright information
• Fixed: ESET Cloud Administrator (ECA) server does not receive all "Web protection" threats
• Fixed: "Web protection" threat details view in the webconsole displays an unexpected error
• Fixed: An uncaught exception occurs when working with ECA
• Fixed: Indonesian language support is missing in product installation filters
• Fixed: Server Device Status chart is missing
ESET Cloud Administrator 1.1.356.0
• FIXED: Issue with too many notifications send from one incident.
ESET Cloud Administrator 1.1.350.0
• New version of ESET Management Agent fixing various installation/upgrade/repair issues.
• Internal service performance improvements
• Fixed invalid installer CA certificate encoding in GPO installer script
ESET Cloud Administrator 1.1.349
• Various minor performance improvements
ESET Cloud Administrator 1.1.345

9
• Various minor bug fixes
• Wrong information is displayed under "Policy Product" column while creating the ECA Live installer
ESET Cloud Administrator 1.1.343.0
• One-click actions
• New one-click action - One click upgrade option – even from aggregated data.
• New One-click actions to resolve "resolvable" actions – activate, reboot, update OS, or various protection
issues
• Hardware inventory
• Redesigned client details section
• New "incident overview" dashboard, with new types of graphical elements, and one-click navigation to threats
• Improved Automatic resolving of handled threats
• Option to generate live installer without security product selected
• New status overview section
• Live installer now support offline cache to speed up the deployment
• Overall UI improvements (polished UI, new vector icons, updated menus)
• Updated "overview" dashboard with one click navigation & Configurable RSS feed
• Redesigned quick links & help links
• New layout for wizard elements
• Ability to switch ECA do different language in EBA (support for NEW languages)
• Automatic detection of "machine cloning"
• Ability to send e-mail directly from ECA when sending installer
• Automatic log-outs
• New more streamlined way when adding computers or using introductory wizard
• Redesigned "filter bar" with the option to remove / reset / save filter presets + "category filter" moved to
"filters"
• New columns for number / highest severity of alerts, cloning questions, and hardware detection reliability
status
• Enhanced filtering options by product name, version, number of alerts, policies, threats, & other options
• New "remove computer from management" wizard, showing clear steps how to correctly remove devices from
ECA
• Redesigned task wizard
• New task types - Diagnostic (enable diagnostic / log collector)
• Section "logs" now includes tabs to display "log collector" and new section for "diagnostic logs"
• Alerts - Alert (problem) details are reported from the supported security products
• New dynamic groups for desktops and servers
• Questions to resolve conflicts

10
• Possible to locate threats detected by the same scan
• Added current detection engine version and a hash value
• Possibility to filter by cause, threat type, scan, scanner and define more granular criteria for the time filter in
threats
• Possibility to collapse and expand all reports in one click
• Software installation task executes a "pre-execution check", and reports "task failed" with further details
• New report template categories Hardware Inventory, Cloning Detection
• Restyled report creation wizard
• Extended options for filtering for specific values
• Redesigned installer generation flow
• Ability to configure LiveGrid and PUA settings when creating live installer
• Ability to configure Live Installer proxy settings during the installer creation
• Support for GPO (Group policy)
• New filter to "hide not-assigned policies"
• Policy details showing "assigned to" (combines computers / groups) and "applied on" (actually applied targets)
• New predefined policies for optimal usage of ESET Live Grid, and few tweaks to existing recommended
templates for maximum protection
• Possibility to allow "local lists"
• Possible to edit multiple notifications at once
• New announcement channel to inform users about planned outages and other important events
• Improved migration from ERA6 (ESMC) managed environment when executing live installers
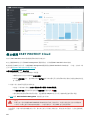
服务的可用性
可用性
我们的目标是提供 99.5% 的服务可用性。我们的努力和定义明确的流程会推动实现这一目标。如果 ESET PROTECT
Cloud 服务中断,端点仍保持安全且不受影响。
维护
ESET PROTECT Cloud 服务遵循日常维护程序。超过 15 分钟的所有维护窗口都会事先告知控制台管理员。维护窗口期
间的停机不会影响我们订立的目标可用性。维护将在周末和工作时间之外执行(美国数据中心 - 美国夜间;欧盟数据
中心 - 欧盟夜间)。
ESET PROTECT Cloud 简介
欢迎使用 ESET PROTECT Cloud。借助 ESET PROTECT Cloud,可以从一个中心位置管理联网环境(最多包含 10,000 台
设备)中工作站和服务器上的 ESET 产品。通过使用ESET PROTECT Cloud Web 控制台,可以部署 ESET 解决方案、管
理任务、强制执行安全策略、监控系统状态,以及快速响应远程计算机上的问题或威胁。
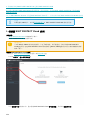
ESET PROTECT Cloud 由以下组件构成:
ESET PROTECT Cloud作为服务
ESET PROTECT Cloud Web 控制台

11
• Web 控制台能够解释ESET PROTECT Cloud数据库中储存的数据。它能够在清楚的面板和报告中显示大量的数据,
还能执行策略和实施服务器代理和其他 ESET 应用程序上的任务。
ESET PROTECT Live Installer
• 是一个小应用程序,该程序由ESET Management服务器代理和已简化且易于使用的程序包中的企业端点产品构成。
• ESET Management 服务器代理是一个不具有图像用户界面的小应用程序,能够执行已连接的客户端上的ESET
PROTECT Cloud 命令。它能够执行任务,从 ESET 应用程序中收集日志,解释和强制执行策略并执行其他有效任务
如软件部署和一般计算机监测。
• 它是易于下载、已经预配置的程序包,包含服务器代理和安全产品(在安装过程中下载)并采用已经简化的安装
程序形式,该种形式将会在实现要求的最低用户互动的情况下自动与适合的云实例相连并会采用有效的许可证激活
其自身。安装程序将识别正确的平台,并下载适合的安全产品安装程序包。
• 服务器代理是一种轻量级的应用程序,能够促进客户端计算机上 ESET 安全产品和 ESET PROTECT Cloud 之间的
所有通信。
ESET 安全产品
• ESET 安全产品保护客户端计算机和服务器免受威胁的侵害。
• ESET PROTECT Cloud支持如下ESET 安全产品。
ESET Business Account
• 企业客户或身份提供者进入ESET PROTECT Cloud的中心进入点。
• 作为向企业客户提供的单点登录服务,以便查看它们的许可证、已激活的服务和实施用户管理等。
• 要求 ESET business account 激活ESET PROTECT Cloud实例。
ESET Remote Deployment Tool
• 可向网络远程部署 ESET PROTECT Live Installer 的工具。
• 拥有远程绘制网络并与 AD 同步或支持产品部署所在的目标的导入的能力

12
ESET PROTECT Cloud 中的新功能
重命名 ESET Cloud Administrator
ESET Cloud Administrator 已重命名为“ESET PROTECT Cloud”。 产品和服务不断发展,以满足新的市场和客户需求。我
们决定重命名我们的解决方案,以便更好地适配当前功能和我们计划的新功能。
适用于的远程移动设备管理 Android
使用适用于 Android 的 ESET Endpoint Security 管理和保护 Android 移动设备。通过电子邮件或二维码快速部署到一
个或多个设备。初始配置和可扩展性可为小型环境中的操作提供显著优势,同时也适用于大型站点部署。了解更多
ESET Full Disk Encryption 对于 macOS
我们计划扩展平台覆盖范围并添加 FileVault (适用于 macOS 的本地加密)管理,以提高组织的数据安全性。了解更多
支持 ESET Dynamic Threat Defense
一种附加付费服务,通过利用基于云的沙盒技术来检测从未见过的新威胁类型,从而为诸如 Mail Security 和 Endpoint
之类的 ESET 产品提供额外一层安全保护。通过采用以下技术来确保您公司的安全性永不落后:基于行为的检测、机器
学习、零日威胁检测和云沙盒。了解更多
管理多达 10,000 台设备
根据 ESET PROTECT Cloud 中的许可证,管理并保护多达 10,000 台设备。

13
管理服务器代理自动更新
自动更新将有助于实现所需的兼容性和最高安全性。ESET 会集中管理最新的服务器代理版本并将其部署到生产。智能设
计将确保所有更新都会分阶段部署,并在更长一段时间内进行分发。
管理员可以在中心自动部署开始之前手动更新服务器代理。
高级功能
一些新功能侧重于满足大型网络的需求,以便可以进行更多自定义。这些功能都会并入现有用户界面中。
动态组管理
创建自定义动态组,以便更好地组织您的设备。了解更多
通知管理
创建自定义电子邮件通知,以让您及时了解网络状态。了解更多
适用于管理员的自定义访问权限
扩展功能可用于自定义访问权限,并为使用 ESET PROTECT Cloud 的管理员定义权限集。确定管理员可以访问的功能或
设备以及允许执行的操作。了解更多
Active Directory 扫描(计算机)
扫描 Active Directory,然后将多台计算机一次添加到 ESET PROTECT Cloud 中。了解更多
审核日志
新功能可帮助管理员识别和跟踪 ESET PROTECT Cloud 中的活动。轻松导航到运行任务、更改的策略、已解决的检测、
添加的用户或计算机,然后根据需要进行调整或更正。 了解更多
系统日志(日志导出)
收集 ESET PROTECT Cloud 中与安全有关的事件并将其发送到 SIEM 工具,其中安全专家可以对这些事件进行分析。在
运行 ESET 产品的任何托管客户端计算机上生成事件。了解更多
排除防火墙威胁
添加了从检测列表中排除防火墙威胁的功能。 了解更多
支持 ESET Business Account 站点
现在,可以导入 ESET Business Account 的完整结构,包括在站点之间分发许可证席位。
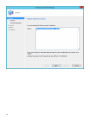
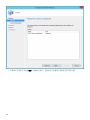
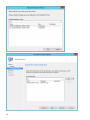
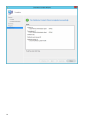
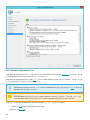
受支持的 Web 浏览器、ESET 安全产品和语言
ESET PROTECT Cloud Web 控制台可以在以下 Web 浏览器中运行:
Web 浏览器
Mozilla Firefox
Microsoft Edge
Google Chrome
Safari
Opera
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
 91
91
-
 92
92
-
 93
93
-
 94
94
-
 95
95
-
 96
96
-
 97
97
-
 98
98
-
 99
99
-
 100
100
-
 101
101
-
 102
102
-
 103
103
-
 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
 109
109
-
 110
110
-
 111
111
-
 112
112
-
 113
113
-
 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
 135
135
-
 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
 142
142
-
 143
143
-
 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
-
 151
151
-
 152
152
-
 153
153
-
 154
154
-
 155
155
-
 156
156
-
 157
157
-
 158
158
-
 159
159
-
 160
160
-
 161
161
-
 162
162
-
 163
163
-
 164
164
-
 165
165
-
 166
166
-
 167
167
-
 168
168
-
 169
169
-
 170
170
-
 171
171
-
 172
172
-
 173
173
-
 174
174
-
 175
175
-
 176
176
-
 177
177
-
 178
178
-
 179
179
-
 180
180
-
 181
181
-
 182
182
-
 183
183
-
 184
184
-
 185
185
-
 186
186
-
 187
187
-
 188
188
-
 189
189
-
 190
190
-
 191
191
-
 192
192
-
 193
193
-
 194
194
-
 195
195
-
 196
196
-
 197
197
-
 198
198
-
 199
199
-
 200
200
-
 201
201
-
 202
202
-
 203
203
-
 204
204
-
 205
205
-
 206
206
-
 207
207
-
 208
208
-
 209
209
-
 210
210
-
 211
211
-
 212
212
-
 213
213
-
 214
214
-
 215
215
-
 216
216
-
 217
217
-
 218
218
-
 219
219
-
 220
220
-
 221
221
-
 222
222
-
 223
223
-
 224
224
-
 225
225
-
 226
226
-
 227
227
-
 228
228
-
 229
229
-
 230
230
-
 231
231
-
 232
232
-
 233
233
-
 234
234
-
 235
235
-
 236
236
-
 237
237
-
 238
238
-
 239
239
-
 240
240
-
 241
241
-
 242
242
-
 243
243
-
 244
244
-
 245
245
-
 246
246
-
 247
247
-
 248
248
-
 249
249
-
 250
250
-
 251
251
-
 252
252
-
 253
253
-
 254
254
-
 255
255
-
 256
256
-
 257
257
-
 258
258
-
 259
259
-
 260
260
-
 261
261
-
 262
262
-
 263
263
-
 264
264
-
 265
265
-
 266
266
-
 267
267
-
 268
268
-
 269
269
-
 270
270
-
 271
271
-
 272
272
-
 273
273
-
 274
274
-
 275
275
-
 276
276
-
 277
277
-
 278
278
-
 279
279
-
 280
280
-
 281
281
-
 282
282
-
 283
283
-
 284
284
-
 285
285
-
 286
286
-
 287
287
-
 288
288
-
 289
289
-
 290
290
-
 291
291
-
 292
292
-
 293
293
-
 294
294
-
 295
295
関連論文
-
ESET Endpoint Security for macOS 6.11 取扱説明書
-
ESET Endpoint Security for macOS 6.11 取扱説明書
-
ESET Security Management Center 7.2 Administration Guide
-
ESET Endpoint Antivirus for macOS 6.11 取扱説明書
-
ESET Endpoint Antivirus for macOS 6.11 取扱説明書
-
ESET Endpoint Security for Android 4.x Google Play download 取扱説明書
-
ESET Security Management Center 7.1 Administration Guide
-
ESET PROTECT 8.0 Administration Guide
-
ESET PROTECT 8.0 Administration Guide
-
ESET PROTECT 8.0 Administration Guide







































































































































































































































































































