
.......................................................5ESET Cyber Security1.
....................................................................................................56 1.1
....................................................................................................51.2
.......................................................62.
....................................................................................................62.1
....................................................................................................72.2
.......................................................83.
.......................................................94.
.......................................................105.
....................................................................................................105.1
....................................................................................................105.2
....................................................................................................115.3
.......................................................126.
....................................................................................................126.1
..............................................................................12
6.1.1
..................................................................................12
6.1.1.1
..............................................................................12
6.1.2
..............................................................................13
6.1.3
..................................................................................13
6.1.3.1
..................................................................................13
6.1.3.2
..................................................................................13
6.1.3.3
..................................................................................13
6.1.3.4
..............................................................................14
6.1.4
..................................................................................14
6.1.4.1
........................................................................14
6.1.4.1.1
........................................................................15
6.1.4.1.2
..................................................................................15
6.1.4.2
..................................................................................15
6.1.4.3
..............................................................................16ThreatSense
6.1.5
..................................................................................16
6.1.5.1
..................................................................................16
6.1.5.2
..................................................................................16
6.1.5.3
..................................................................................17
6.1.5.4
..................................................................................17
6.1.5.5
..................................................................................17
6.1.5.6
..............................................................................17
6.1.6
....................................................................................................186.2
.......................................................197.
.......................................................20Web 8.
....................................................................................................20Web 8.1
..............................................................................20
8.1.1
..............................................................................20URL
8.1.2
....................................................................................................208.2
..............................................................................21POP3
8.2.1
..............................................................................21IMAP
8.2.2
.......................................................229.
....................................................................................................229.1
..............................................................................22
9.1.1
....................................................................................................229.2
....................................................................................................22
ESET Cyber Security9.3
....................................................................................................239.4
.......................................................2410.
....................................................................................................2410.1
..............................................................................24
10.1.1
..............................................................................24
10.1.2
....................................................................................................2510.2
..............................................................................25
10.2.1
..............................................................................26
10.2.2
....................................................................................................2610.3
..............................................................................26
10.3.1
..............................................................................26
10.3.2
..............................................................................27
10.3.3
....................................................................................................2710.4
....................................................................................................27Live Grid10.5
..............................................................................28Live Grid
10.5.1
.......................................................2911.
....................................................................................................2911.1
..............................................................................29
11.1.1
..............................................................................29
11.1.2
....................................................................................................3011.2
....................................................................................................3011.3
.......................................................3112.
....................................................................................................3112.1
....................................................................................................31Proxy 12.2
.......................................................3213.
....................................................................................................3213.1
..............................................................................32
13.1.1
..............................................................................32
13.1.2
..............................................................................32
13.1.3
..............................................................................33Rootkit
13.1.4
..............................................................................33
13.1.5
..............................................................................33
13.1.6
..............................................................................33
13.1.7
..............................................................................33
13.1.8
....................................................................................................3413.2
..............................................................................34DoS
13.2.1
..............................................................................34DNS Poisoning
13.2.2
..............................................................................34
13.2.3
..............................................................................34TCP
13.2.4

..............................................................................34SMB Relay
13.2.5
..............................................................................35ICMP
13.2.6
....................................................................................................3513.3
..............................................................................35
13.3.1
..............................................................................35
13.3.2
..............................................................................36
13.3.3
..............................................................................36
13.3.4

8
3.
[ ] macOS (
) ESET Cyber Security [ ]
· - XXXX-XXXX-XXXX-XXXX-XXXX XXXX-XXXXXXXX
· - ESET Cyber Security [
] my.eset.com
· BETA - ESET Cyber Security
ESET Cyber Security
· - [ ] ESET
· -

9
4.
ESET Cyber Security
· ESET Cyber Security CD/DVD Finder [ ]
· ESET Cyber Security (
.dmg
) [ ]
· [Finder] [ ] Ctrl ESET Cyber Security [
] Contents > Helpers Uninstaller

10
5.
ESET Cyber Security
· Web
·
· [ ]
·
·
·
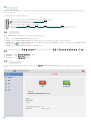
5.1
ESET Cyber Security
·
cmd+,
- ESET Cyber Security
·
cmd+O
- ESET Cyber Security GUI
·
cmd+Q
- ESET Cyber Security GUI macOS ( ) ESET Cyber
Security
·
cmd+W
- ESET Cyber Security GUI
[ ] [ ] > [ ] > [
]
·
cmd+alt+L
- [ ]
·
cmd+alt+S
- [ ]
·
cmd+alt+Q
- [ ]
5.2
[ ] ESET Cyber Security
14
24 25 26 27

13
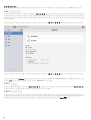
6.1.3
ThreatSense ( ThreatSense
)
[ ] [ ] [ ]
( ) ( ) ESET Cyber Security
[ ] (
[ ] > [ ] [ ] [ ])
Real-time
· [ ] -
· [ ] - CD DVD USB
· [ ] -
[ ] > [ ](
cmd+,
) > [
] [ ] [ ] ( )
6.1.3.1
ThreatSense [ ] [ ]
[ ] ThreatSense
[ ]
[ ThreatSense ] - [ ]
ESET Live Grid
-
macOS 10.10
Microsoft Word 2011 Word 2016
6.1.3.2
ESET Cyber Security
ESET Cyber Security
[ ] [ ] [ ] [ ] > [ ]> [
])
6.1.3.3
eicar.com ESET Cyber Security
EICAR (European
Institute for Computer Antivirus Research)
6.1.3.4
[ ] >
[ ] [ ] [ ] [ ] [
]
16
13
16

16
6.1.5 ThreatSense
ThreatSense ESET
( )
ThreatSense
Rootkit
ThreatSense
·
·
·
[ > ] (
cmd+,
) [ ] [
] [ ] ThreatSense [ ] ThreatSense (
) ThreatSense
· [ ] -
· -
· -
· Web
·
ThreatSense
Runtime Packer
ThreatSense
6.1.5.1
[ ]
· [ ] - ( )
· [ ] - ( )
· [ ] - ( )
· [ ] - ( ) (.rar zip arj tar )
· [ ] - ( )
· [Runtime Packers] - Runtime Packer ( )
UPX yoda ASPack FGS
6.1.5.2
[ ]
· ( )
· ESET
6.1.5.3
3
· -
· -
· - ( )

18
-
[ ]
6.2
ESET Cyber Security (CD DVD USB iOS )
[ ]
( ) [ ] > [ ]> [ ] [
]
USB CD-ROM [CD-ROM]

19
7.
( )
PIN
([ ] > [ ]> ) ESET

20
8. Web
Web [ ] > [Web ] [
]
· Web - Web HTTP
· - POP3 IMAP
· - ESET
8.1 Web
Web Web HTTP ( )
HTTP URL Web
8.1.1
[ ] HTTP 80 8080
3128
8.1.2 URL
[URL ] HTTP
[ URL] URL [ URL ]
[ ] [
]
*
( )
?
( )
?
8.2
POP3 IMAP
ThreatSense POP3 IMAP
ThreatSense [ ]
[ ]
HTML
· [ ]
· [ ]
· [ ]
[ ]
[ ]
POP3 IMAP
· POP3
· IMAP
20 20
21
21
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
関連論文
-
ESET Cyber Security for macOS ユーザーガイド
-
ESET Cyber Security Pro for macOS 6 取扱説明書
-
ESET Cyber Security for macOS 6 取扱説明書
-
ESET Cyber Security for macOS クイックスタートガイド
-
ESET Cyber Security Pro for macOS 6 取扱説明書
-
ESET Cyber Security for macOS 6 取扱説明書
-
ESET Cyber Security for macOS 6 取扱説明書
-
ESET Cyber Security Pro for macOS 6 取扱説明書
-
ESET Cyber Security for macOS ユーザーガイド













































