
ESET MAIL SECURITY
Copyright ©2020 by ESET, spol. s r.o.
ESET Mail Security ESET, spol. s r.o.
www.eset.com
ESET, spol. s r.o.
www.eset.com/support
2020/4/17

..........................................................5
1.
..........................................................6
2.
...........................................................................62.1
...........................................................................82.2
...........................................................................82.3
...........................................................................9ESET Mail Security Exchange Server 2.4
...........................................................................10Exchange Server 2.5
...........................................................................10POP3 Connector 2.6
...........................................................................112.7
...........................................................................122.8
................................................................................12
2.8.1
................................................................................13
2.8.2
................................................................................14
2.8.3
................................................................................15
Office 365 2.8.4
..........................................................16
3.
...........................................................................173.1
...........................................................................18ESET Mail Security 3.2
................................................................................22
3.2.1
...........................................................................233.3
................................................................................24
3.3.1
...........................................................................273.4
................................................................................28
ESET Business Account3.4.1
................................................................................28
3.4.2
................................................................................28
3.4.3
................................................................................29
3.4.4
...........................................................................293.5
................................................................................30
ESET Security Management Center3.5.1
................................................................................32
ESET 3.5.2
...........................................................................343.6
...........................................................................343.7
...........................................................................34DAG 3.8
..........................................................35
4.
...........................................................................354.1
...........................................................................36ESET Security Management Center 4.2
...........................................................................374.3
................................................................................38
4.3.1
................................................................................39
Windows 4.3.2
..........................................................40
ESET Mail Security5.
...........................................................................405.1
................................................................................42
5.1.1
...........................................................................445.2
................................................................................47
5.2.1
...........................................................................48 [ ]5.3
...........................................................................495.4
...........................................................................525.5
................................................................................53
5.5.1
................................................................................53
5.5.2
................................................................................54
5.5.3
............................................................................54
5.5.3.1
................................................................................54
Web 5.5.4
................................................................................55
5.5.5
................................................................................56
5.5.6
...........................................................................565.6
................................................................................58
5.6.1
................................................................................59
5.6.2
................................................................................61
5.6.3
................................................................................62
5.6.4
............................................................................64
5.6.4.1
............................................................................65
5.6.4.2
............................................................................66
5.6.4.3
............................................................................66
5.6.4.4
............................................................................69
5.6.4.5
................................................................................71
ESET Shell5.6.5
............................................................................73
5.6.5.1
............................................................................77
5.6.5.2
............................................................................79
5.6.5.3
................................................................................80
ESET Dynamic Threat Defense5.6.6
................................................................................81
ESET SysInspector5.6.7
................................................................................82
ESET SysRescue Live5.6.8
................................................................................82
5.6.9
............................................................................83
5.6.9.1
............................................................................85
5.6.9.1.1
............................................................................85
5.6.9.1.2
............................................................................86
5.6.9.1.3
............................................................................86
5.6.9.1.4
............................................................................86
5.6.9.1.5
............................................................................86
5.6.9.1.6
................................................................................87
5.6.10
............................................................................87
5.6.10.1
............................................................................88
5.6.10.2
............................................................................88
5.6.10.3
............................................................................88
5.6.10.4
............................................................................89
5.6.10.5
................................................................................89
5.6.11
..........................................................91
6.
...........................................................................916.1
...........................................................................926.2
...........................................................................946.3
................................................................................95
6.3.1
................................................................................97
6.3.2
................................................................................100
6.3.3
................................................................................101
SPF DKIM6.3.4
................................................................................102
6.3.5
...........................................................................1036.4
...........................................................................1046.5
................................................................................106
6.5.1
................................................................................109
6.5.2
................................................................................111
6.5.3
...........................................................................1136.6
................................................................................115
6.6.1
...........................................................................1166.7
................................................................................117
6.7.1
...........................................................................1176.8
................................................................................119
6.8.1
................................................................................121
Office 365 6.8.2
................................................................................122
6.8.3
................................................................................122
Proxy 6.8.4
................................................................................122
6.8.5

...........................................................................1236.9
................................................................................124
6.9.1
............................................................................125
6.9.1.1
............................................................................125
Web 6.9.1.2
............................................................................130
6.9.1.2.1
............................................................................131
Web 6.9.1.2.2
................................................................................133
MS Exchange 6.9.2
............................................................................133
6.9.2.1
............................................................................134
Proxy 6.9.2.2
................................................................................134
6.9.3
...........................................................................1356.10
...........................................................................1356.11
...........................................................................1356.12
..........................................................136
7.
...........................................................................1367.1
................................................................................137
7.1.1
................................................................................138
7.1.2
............................................................................139
7.1.2.1
................................................................................140
7.1.3
................................................................................141
7.1.4
................................................................................141
7.1.5
................................................................................142
7.1.6
............................................................................143
ThreatSense 7.1.6.1
............................................................................146
ThreatSense 7.1.6.1.1
............................................................................146
7.1.6.1.2
................................................................................146
7.1.7
............................................................................148
7.1.7.1
................................................................................149
7.1.8
............................................................................150
7.1.8.1
............................................................................151
7.1.8.2
............................................................................152
7.1.8.3
............................................................................154
7.1.8.4
............................................................................154
7.1.8.5
............................................................................154
7.1.8.5.1
............................................................................155
7.1.8.6
............................................................................155
7.1.8.7
................................................................................155
Hyper-V 7.1.9
................................................................................157
HIPS7.1.10
............................................................................158
HIPS 7.1.10.1
............................................................................161
HIPS 7.1.10.2
...........................................................................1617.2
................................................................................164
7.2.1
................................................................................164
7.2.2
................................................................................164
7.2.3
...........................................................................1667.3
................................................................................167
IDS 7.3.1
................................................................................167
IP 7.3.2
...........................................................................168Web 7.4
................................................................................168
7.4.1
............................................................................169
Web 7.4.1.1
................................................................................169
SSL/ TLS7.4.2
............................................................................170
7.4.2.1
............................................................................171
SSL 7.4.2.2
................................................................................171
7.4.3
............................................................................172
7.4.3.1
............................................................................173
7.4.3.2
............................................................................173
MS Outlook 7.4.3.3
............................................................................173
Outlook Express Windows Mail 7.4.3.4
............................................................................174
7.4.3.5
............................................................................174
7.4.3.6
................................................................................174
Web 7.4.4
............................................................................175
URL 7.4.4.1
............................................................................176
7.4.4.1.1
................................................................................177
Web 7.4.5
...........................................................................1787.5
................................................................................178
7.5.1
................................................................................180
7.5.2
...........................................................................1817.6
................................................................................181
7.6.1
................................................................................181
Microsoft Windows 7.6.2
................................................................................181
ESET CMD7.6.3
................................................................................183
ESET RMM7.6.4
................................................................................184
WMI 7.6.5
............................................................................184
7.6.5.1
............................................................................190
7.6.5.2
................................................................................190
ERA/ ESMC 7.6.6
................................................................................191
7.6.7
................................................................................194
7.6.8
............................................................................196
7.6.8.1
................................................................................199
Proxy 7.6.9
................................................................................199
7.6.10
............................................................................200
7.6.10.1
............................................................................200
7.6.10.2
............................................................................200
7.6.10.3
............................................................................201
7.6.10.4
................................................................................202
7.6.11
................................................................................202
7.6.12
................................................................................203
7.6.13
...........................................................................2047.7
................................................................................205
7.7.1
................................................................................205
7.7.2
................................................................................206
ESET Shell7.7.3
................................................................................206
GUI7.7.4
................................................................................206
7.7.5
............................................................................207
7.7.5.1
................................................................................208
7.7.6
...........................................................................2097.8
...........................................................................2097.9
................................................................................210
7.9.1
................................................................................210
ESET Mail Security7.9.2
...........................................................................2117.10

6
2.
Microsoft Exchange Server ESET Mail Security 7
ESET Mail Security
ESET Mail Security
ESET Mail Security Microsoft Exchange Server 2007 Microsoft
Exchange Server Exchange (mailbox hub edge)
ESET Mail Security Microsoft Exchange Server (
Web )
ESMC ESET Mail Security ESET Mail Security
(RMM)
2.1
ESET Mail Security
64
Rootkit
UEFI
DNA
(AMSI)
ESET Mail Security
ESET Mail
Security Virus Bulletin
VBSpam+ 99.99%
ESET Mail Security
(RBL DNSBL
SPF DKIM )
ESET Mail Security
ESET
ESET Mail Security
(URL)
(Arcsight)
(CEF)
Micro Focus ArcSight
SmartConnector ArcSight

7
ESET Mail Security Microsoft Exchange Server
Office 365
Exchange
ESET Dynamic Threat
Defense (EDTD)
ESET ESET Mail Security
ESET Dynamic Threat Defense
ESET Dynamic Threat Defense
ESET Mail Security
Web
Web
Web
EWS (Exchange Web ) API
HTTP/HTTPS Microsoft Exchange Server
ESET
ESET ESET File Security for Microsoft
Windows Server
ESET
(.exe)
eShell ESET Shell
ESET Mail Security eShell 2.0 eShell
ESET
ESET Security Management
Center
ESET Security Management Center ( )
ESET Security Management Center

9
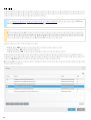
2.4 ESET Mail Security Exchange Server
Microsoft Exchange Server ESET Mail Security
ESET Mail Security Exchange Server
[Exchange Server
]
Microsoft Exchange Server 2007 (
)
Microsoft Exchange Server 2007
(Edge)
Microsoft Exchange Server 2007
(Hub)
Microsoft Exchange Server 2007 (
)
Microsoft Exchange Server 2010 (
)
Microsoft Exchange Server 2010
(Edge)
Microsoft Exchange Server 2010
(Hub)
Microsoft Exchange Server 2010 (
)
Microsoft Exchange Server 2013 (
)
Microsoft Exchange Server 2013
(Edge)
Microsoft Exchange Server 2013 (
)
Microsoft Exchange Server 2016
(Edge)
Microsoft Exchange Server 2016 (
)
Microsoft Exchange Server 2019
(Edge)
Microsoft Exchange Server 2019 (
)

10
[Exchange Server
]
Windows Small Business Server 2008
SP2
Windows Small Business Server 2011
2.5 Exchange Server
Edge Hub
Exchange Exchange ESET Mail Security
ESET Mail Security
ESET Mail Security
SMTP
Microsoft Exchange 2013 ESET Mail Security CAS (
) Microsoft Exchange Server
2.6 POP3 Connector
Microsoft Windows Small Business Server (SBS) POP3 POP3
Microsoft POP3 SBS
ESET Mail Security Microsoft SBS POP3 ( ) Microsoft POP3
POP3 SMTP POP3
Microsoft Exchange Server
ESET Mail Security SBS Gmail.com Outlook.com Yahoo.com
Yandex.com gmx.de
· Microsoft Windows Small Business Server 2008 R2
· Microsoft Windows Small Business Server 2011
Microsoft SBS POP3 [F5]
[ ] [ ] > [ ] > [ ] [
] [ ]
POP3
POP3 P3SS ( Microsoft SBS POP3 )

12
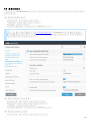
2.8
ESET Mail Security
·
·
·
· Office 365
ESET Mail Security Microsoft Exchange Server
2.8.1
Microsoft Exchange Server Microsoft Exchange Server
Microsoft Exchange Server VSAPI
· ( )
· Microsoft Exchange Server
· ( Microsoft Exchange Server )
Microsoft Exchange Server 2013 2016 2019
[Exchange Server
]
Microsoft Exchange Server 2007 (
)
Microsoft Exchange Server 2007 (
)
Microsoft Exchange Server 2010 (
)
Microsoft Exchange Server 2010 (
)
Windows Small Business Server 2008
SP2
Windows Small Business Server 2011
Exchange Server (
)

13
2.8.2
SMTP Microsoft Exchange Server 2007 2010
Microsoft Exchange Server
SMTP
VSAPI Microsoft Exchange Server SMTP
SMTP
Microsoft Exchange Server 2007
Exchange Server ( )
[Exchange Server
]
Microsoft Exchange Server 2007
(Hub)
Microsoft Exchange Server 2007
(Edge)
Microsoft Exchange Server 2010 (
)
Microsoft Exchange Server 2013 (
)
Microsoft Exchange Server 2013
(Edge)
Microsoft Exchange Server 2013 (
)
Microsoft Exchange Server 2016
(Edge)
Microsoft Exchange Server 2016 (
)
Microsoft Exchange Server 2019
(Edge)
Microsoft Exchange Server 2019 (
)
Windows Small Business Server
2008 SP2
Windows Small Business Server
2011

14
2.8.3
Exchange
Microsoft Exchange Server 2007 Exchange Server
( )
[Exchange Server
]
Microsoft Exchange Server 2007
( )
Microsoft Exchange Server 2007
(Hub)
Microsoft Exchange Server 2007
( )
Microsoft Exchange Server 2010
( )
Microsoft Exchange Server 2010
(Hub)
Microsoft Exchange Server 2010
( )
Microsoft Exchange Server 2013
( )
Microsoft Exchange Server 2013
( )
Microsoft Exchange Server 2016
( )
Microsoft Exchange Server 2019
( )
Windows Small Business Server
2008 SP2
Windows Small Business Server
2011

16
3.
· ESET Mail Security ESET .msi
· ESET Mail Security
· Administrator
Administrator Administrator ( Administrator
) ( Administrators )
Administrator Administrator
· ESET Mail Security
· ESET AV Remover
ESET AV Remover
· Windows Server 2016 ESET Mail Security Microsoft Windows
Defender Windows Defender ATP
· ESET Mail Security Microsoft Exchange Server
· ESET Mail
Security
ESET Mail Security
· (GUI)
·
ESET Mail Security
ESET Mail Security
ESET Mail Security ESET Mail
Security
·
ESET Mail Security
ESET Mail Security
·
·
ESET Mail Security

17
·
ESET Mail Security
3.1
· Microsoft Windows Server 2019 (Server Core )
· Microsoft Windows Server 2016
· Microsoft Windows Server 2012 R2
· Microsoft Windows Server 2012
· Microsoft Windows Server 2008 R2 SP1
· Microsoft Windows Server 2008 SP2 (x64)
· Microsoft Windows Small Business Server 2011 (x64)
· Microsoft Windows Small Business Server 2008 SP2 (x64)
Microsoft Exchange Server
· Microsoft Exchange Server 2019 CU1, CU2, CU3, CU4, CU5
· Microsoft Exchange Server 2016 CU1, CU2, CU3, CU4, CU5, CU6, CU7, CU8, CU9, CU10, CU11, CU12, CU13, CU14,
CU15, CU16
· Microsoft Exchange Server 2013 CU2, CU3, CU5, CU6, CU7, CU8, CU9, CU10, CU11, CU12, CU13, CU14, CU15, CU16,
CU17, CU18, CU19, CU20, CU21, CU22, CU23
· Microsoft Exchange Server 2010 SP1, SP2, SP3 UR27
· Microsoft Exchange Server 2007 SP1 SP2 SP3
ESET Mail Security Microsoft Exchange Server 2013 SP1 ( CU4)
Intel AMD x86 x64
256 MB
700 MB
800 x 600
ESET Mail Security Microsoft Exchange Server Microsoft
Microsoft Exchange Server 2007
Microsoft Exchange Server 2010
Microsoft Exchange Server 2013
Microsoft Exchange Server 2016
Microsoft Service Pack ESET
Windows

18
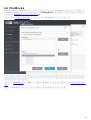
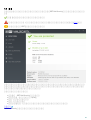
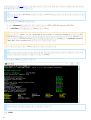
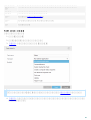
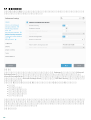
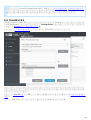
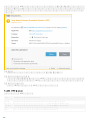
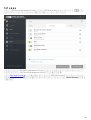
3.2 ESET Mail Security
GUI .msi ESET Mail Security
1. [ ] [ ]
2. [ ] > [ ] [ ] ( [ ] > [ ]
[ ] ) ESET Mail Security [ ]
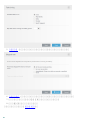
ESET Mail Security
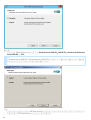
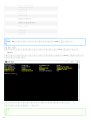
3. [ ] [ ]
[ ]

20
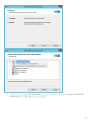
[ ]
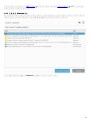
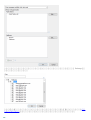
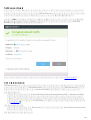
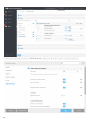
ESET Mail Security Windows Server 2008 SP2 2008 R2 SP1 Windows Small Business
Server 2008 SP2 2011
Windows Server 2008 SP2 Windows Server 2008 R2 SP1 [ ] ([ ]
) [ ]
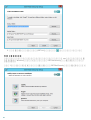
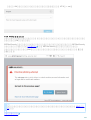
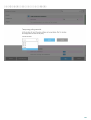
ESET Mail Security
ESET Mail Security
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
 91
91
-
 92
92
-
 93
93
-
 94
94
-
 95
95
-
 96
96
-
 97
97
-
 98
98
-
 99
99
-
 100
100
-
 101
101
-
 102
102
-
 103
103
-
 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
 109
109
-
 110
110
-
 111
111
-
 112
112
-
 113
113
-
 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
 135
135
-
 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
 142
142
-
 143
143
-
 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
-
 151
151
-
 152
152
-
 153
153
-
 154
154
-
 155
155
-
 156
156
-
 157
157
-
 158
158
-
 159
159
-
 160
160
-
 161
161
-
 162
162
-
 163
163
-
 164
164
-
 165
165
-
 166
166
-
 167
167
-
 168
168
-
 169
169
-
 170
170
-
 171
171
-
 172
172
-
 173
173
-
 174
174
-
 175
175
-
 176
176
-
 177
177
-
 178
178
-
 179
179
-
 180
180
-
 181
181
-
 182
182
-
 183
183
-
 184
184
-
 185
185
-
 186
186
-
 187
187
-
 188
188
-
 189
189
-
 190
190
-
 191
191
-
 192
192
-
 193
193
-
 194
194
-
 195
195
-
 196
196
-
 197
197
-
 198
198
-
 199
199
-
 200
200
-
 201
201
-
 202
202
-
 203
203
-
 204
204
-
 205
205
-
 206
206
-
 207
207
-
 208
208
-
 209
209
-
 210
210
-
 211
211
ESET Mail Security for Exchange Server 7.0 取扱説明書
- カテゴリー
- ウイルス対策セキュリティソフトウェア
- タイプ
- 取扱説明書
関連論文
-
ESET Mail Security for Exchange Server 7.0 取扱説明書
-
ESET Mail Security for Exchange Server ユーザーガイド
-
ESET Mail Security for Exchange Server ユーザーガイド
-
ESET Mail Security for Exchange Server ユーザーガイド
-
ESET Server Security for Windows Server (File Security) 7.1 取扱説明書
-
ESET Server Security for Windows Server (File Security) 7.2 取扱説明書
-
ESET Mail Security for Exchange Server ユーザーガイド
-
ESET Server Security for Windows Server (File Security) 7.3 取扱説明書
-
ESET Server Security for Windows Server (File Security) 7.3 取扱説明書
-
ESET Server Security for Windows Server (File Security) 7.1 取扱説明書
























































































































































































































