
..........................................................5
ESET Endpoint Security 6.61.
...........................................................................56.6 1.1
...........................................................................51.2
...........................................................................61.3
..........................................................7
ESET Remote Administrator2.
...........................................................................7ESET Remote Administrator Server2.1
...........................................................................8Web Console2.2
...........................................................................8Proxy2.3
...........................................................................92.4
...........................................................................9RD Sensor2.5
..........................................................10
ESET Endpoint Security3.
...........................................................................10ESET AV Remover 3.1
................................................................................11
ESET AV Remover3.1.1
................................................................................13
ESET AV Remover3.1.2
...........................................................................143.2
................................................................................15
3.2.1
...........................................................................18ERA ( )3.3
...........................................................................203.4
...........................................................................213.5
...........................................................................213.6
...........................................................................213.7
................................................................................22
3.7.1
................................................................................24
3.7.2
................................................................................26
3.7.3
................................................................................26
Web 3.7.4
...........................................................................263.8
................................................................................27
ESET Endpoint Security3.8.1
................................................................................27
ESET Endpoint Security3.8.2
................................................................................27
3.8.3
................................................................................27
PC 3.8.4
................................................................................28
3.8.5
................................................................................28
3.8.6
................................................................................29
( 24 )3.8.7
................................................................................29
ESET Endpoint Security
ESET Remote Administrator
3.8.8
................................................................................29
3.8.9
................................................................................30
ESET Endpoint Security
Windows 10
3.8.10
................................................................................30
3.8.11
................................................................................32
3.8.12
...........................................................................34ESET Endpoint Security3.9
................................................................................35
3.9.1
............................................................................35
3.9.1.1
............................................................................36
3.9.1.1.1
............................................................................37
3.9.1.2
............................................................................38
3.9.1.3
............................................................................39
ThreatSense 3.9.1.3.1
............................................................................39
3.9.1.3.2
............................................................................39
3.9.1.3.3
............................................................................39
3.9.1.3.4
............................................................................40
3.9.1.3.5
............................................................................40
3.9.1.4
............................................................................41
3.9.1.4.1
............................................................................42
3.9.1.4.2
............................................................................43
3.9.1.4.3
............................................................................43
3.9.1.5
............................................................................44
3.9.1.5.1
............................................................................45
3.9.1.5.2
............................................................................46
3.9.1.6
............................................................................47
3.9.1.7
............................................................................47
(HIPS)3.9.1.8
............................................................................49
3.9.1.8.1
............................................................................50
HIPS 3.9.1.8.2
............................................................................50
3.9.1.9
............................................................................51
3.9.1.10
............................................................................51
3.9.1.10.1
............................................................................51
3.9.1.11
............................................................................52
3.9.1.12
............................................................................53
ThreatSense 3.9.1.13
............................................................................56
3.9.1.13.1
................................................................................57
3.9.2
............................................................................58
3.9.2.1
............................................................................59
3.9.2.1.1
............................................................................60
3.9.2.2
............................................................................60
3.9.2.2.1
............................................................................61
3.9.2.3
............................................................................61
3.9.2.3.1
............................................................................62
3.9.2.3.2
............................................................................63
3.9.2.4
............................................................................63
3.9.2.5
............................................................................63
3.9.2.6
............................................................................63
3.9.2.6.1
............................................................................66
3.9.2.6.2
............................................................................66
3.9.2.7
............................................................................67
3.9.2.8
............................................................................67
ESET 3.9.2.9
............................................................................68
3.9.2.9.1
............................................................................68
3.9.2.9.2
............................................................................68
3.9.2.9.2.1
............................................................................68
3.9.2.9.3
............................................................................68
PCAP 3.9.2.9.4
............................................................................69
3.9.2.9.5
................................................................................70
Web 3.9.3
............................................................................71
3.9.3.1
............................................................................71
Web 3.9.3.1.1
............................................................................71
3.9.3.1.2
............................................................................72
IP 3.9.3.1.3
............................................................................72
SSL/ TLS3.9.3.1.4
............................................................................73
SSL 3.9.3.1.4.1
............................................................................73
3.9.3.1.4.2
............................................................................74
SSL/ TLS 3.9.3.1.4.3
............................................................................74
3.9.3.2
............................................................................74
3.9.3.2.1
............................................................................75
3.9.3.2.2
............................................................................76
3.9.3.2.3
............................................................................76
3.9.3.2.4
............................................................................78
3.9.3.2.4.1
............................................................................78
3.9.3.2.4.2
............................................................................78
3.9.3.2.4.3
............................................................................79
Web 3.9.3.3
............................................................................79
Web 3.9.3.3.1
............................................................................80
URL 3.9.3.3.2
............................................................................80
3.9.3.4
................................................................................81
Web 3.9.4
............................................................................82
3.9.4.1
............................................................................82
Web 3.9.4.1.1
............................................................................84
3.9.4.2

............................................................................84
URL 3.9.4.3
................................................................................85
3.9.5
............................................................................88
3.9.5.1
............................................................................90
3.9.5.1.1
............................................................................90
3.9.5.1.2
............................................................................90
3.9.5.1.3
............................................................................91
HTTP proxy3.9.5.1.4
............................................................................91
3.9.5.1.5
............................................................................92
3.9.5.1.6
............................................................................93
3.9.5.1.6.1
............................................................................95
3.9.5.1.6.2
............................................................................95
3.9.5.2
................................................................................96
3.9.6
............................................................................97
3.9.6.1
............................................................................98
3.9.6.1.1
............................................................................98
Proxy 3.9.6.2
............................................................................99
3.9.6.3
............................................................................100
3.9.6.4
............................................................................101
3.9.6.5
............................................................................102
ESET SysInspector3.9.6.6
............................................................................102
ESET LiveGrid®3.9.6.7
............................................................................103
3.9.6.8
............................................................................104
3.9.6.9
............................................................................105
3.9.6.10
............................................................................106
3.9.6.11
............................................................................108
3.9.6.12
............................................................................109
Microsoft Windows 3.9.6.13
............................................................................109
ESET CMD3.9.6.14
................................................................................110
3.9.7
............................................................................110
3.9.7.1
............................................................................111
3.9.7.2
............................................................................112
3.9.7.3
............................................................................113
3.9.7.3.1
............................................................................113
3.9.7.4
............................................................................114
3.9.7.5
...........................................................................1143.10
................................................................................114
3.10.1
................................................................................115
3.10.2
................................................................................115
3.10.3
................................................................................116
3.10.4
................................................................................117
3.10.5
................................................................................118
ESET SysInspector3.10.6
............................................................................118
ESET SysInspector 3.10.6.1
............................................................................118
ESET SysInspector3.10.6.1.1
............................................................................118
3.10.6.2
............................................................................119
3.10.6.2.1
............................................................................120
ESET SysInspector 3.10.6.2.2
............................................................................121
3.10.6.2.2.1
............................................................................122
3.10.6.2.3
............................................................................123
3.10.6.3
............................................................................123
3.10.6.4
............................................................................124
3.10.6.4.1
............................................................................124
3.10.6.4.2
............................................................................126
3.10.6.4.3
............................................................................126
3.10.6.5
............................................................................128
ESET SysInspector ESET Endpoint
Security
3.10.6.6
................................................................................128
3.10.7
............................................................................129
RMM 3.10.7.1
............................................................................131
JSON 3.10.7.2
............................................................................131
3.10.7.2.1
............................................................................132
3.10.7.2.2
............................................................................135
3.10.7.2.3
............................................................................135
3.10.7.2.4
............................................................................137
3.10.7.2.5
............................................................................138
3.10.7.2.6
............................................................................139
3.10.7.2.7
............................................................................140
3.10.7.2.8
............................................................................141
3.10.7.2.9
............................................................................142
3.10.7.2.10
............................................................................143
3.10.7.2.11
............................................................................143
3.10.7.2.12
............................................................................144
3.10.7.2.13
...........................................................................1453.11
................................................................................145
3.11.1
............................................................................145
3.11.1.1
............................................................................145
3.11.1.2
............................................................................146
3.11.1.3
............................................................................146
Rootkit3.11.1.4
............................................................................146
3.11.1.5
............................................................................146
3.11.1.6
............................................................................147
3.11.1.7
............................................................................147
3.11.1.8
............................................................................147
3.11.1.9
............................................................................149
3.11.1.10
................................................................................149
3.11.2
............................................................................149
3.11.2.1
............................................................................149
DoS 3.11.2.2
............................................................................149
3.11.2.3
............................................................................149
DNS Poisoning3.11.2.4
................................................................................150
3.11.3
............................................................................150
3.11.3.1
............................................................................150
3.11.3.2
............................................................................150
3.11.3.3
............................................................................151
3.11.3.4
............................................................................151
3.11.3.4.1
............................................................................151
3.11.3.4.2
............................................................................151
3.11.3.4.3
............................................................................152
3.11.3.4.4
............................................................................152
3.11.3.4.5
................................................................................152
ESET 3.11.4
............................................................................152
3.11.4.1
............................................................................152
3.11.4.2
............................................................................152
ESET LiveGrid®3.11.4.3
............................................................................153
3.11.4.4
............................................................................153
Java 3.11.4.5
............................................................................153
3.11.4.6

5
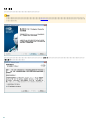
1. ESET Endpoint Security 6.6
ESET Endpoint Security 6 ThreatSense®
ESET Endpoint Security 6
rootkit
ESET Endpoint Security 6 ESET Endpoint Security ESET
Remote Administrator
1.1 6.6
ESET Endpoint Security 6.6 ESET Endpoint Security 6.6
Powershell (wscript.exe cscript.exe) (AMSI)
Web Javascript
(Windows 8.1 10)
( Web )
ESET Endpoint Security
ESET Endpoint Security ESET LiveGrid®
(RMM) ESET Endpoint Security
1.2
ESET Endpoint Security ( )
32-bit (x86) 64-bit (x64) 1 GHz ( 1)
Microsoft® Windows® 10/8.1/8/7/Vista/XP SP3 32 XP SP2 64
ESET
0.3 GB ( 2)
1 GB ( 3)
1024x768
( 4)
(1) Windows XP
(2) ( URL )
(3)
( ) (

7
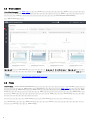
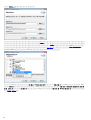
2. ESET Remote Administrator
ESET Remote Administrator (ERA) ESET ESET Remote
Administrator ESET ESET Remote
Administrator ESET
ESET ( )
Microsoft Linux Mac OS
ESET ERA
ESET Remote Administrator
2.1 ESET Remote Administrator Server
ESET Remote Administrator Server ESET Remote Administrator
( ERA ) ERA (
) ERA
ERA ERA
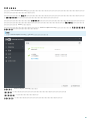
Agent/Proxy/RD Sensor ERA ERA Web Console ( )
Web Console ESET ERA

8
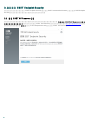
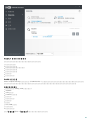
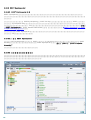
2.2 Web Console
ERA Web Console ERA Web ESET
Web Console ESET
Web ESET Remote Administrator
Web Console
[ ] Web Console [ ]? IPv4/IPv6 [ ]
Enter [ ]
ESET Remote Administrator
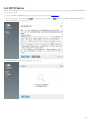
2.3 Proxy
ERA Proxy ESET Remote Administrator ( 10,000 )
ERA Proxy ERA Proxy ERA
ERA Proxy ERA Proxy ERA ERA
Proxy ( ) ERA ERA Proxy
ERA ERA ( ERA Proxy)
ERA Proxy ERA Proxy ERA
ERA Proxy ERA Proxy ESET (
ERA ERA Proxy)

9
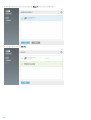
2.4
[ERA ] ESET Remote Administrator ESET (
ESET Endpoint Security) ERA
ESET
ERA ( Proxy)
ESET
1.
2. Proxy
3. Proxy
ESET ESET
ESET Proxy Proxy
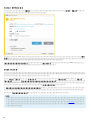
2.5 RD Sensor
RD (Rogue Detection) Sensor ESET Remote Administrator
ESET Remote Administrator
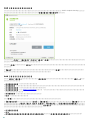
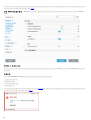
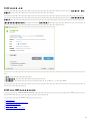
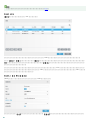
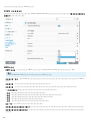
Web Console [ ]
RD Sensor ERA ERA
PC PC PC

12
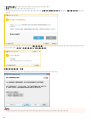
4. [ ]
5. [ ]

18
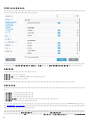
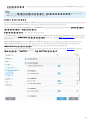
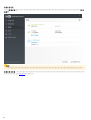
[ ] [ ] [ ]
ESET Endpoint Security [ ]
[ ]
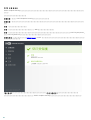
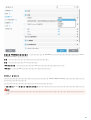
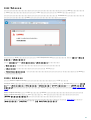
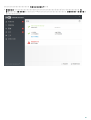
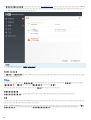
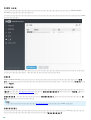
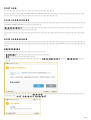
3.3 ERA ( )
? msiexec
APPDIR=<path>
o
o
o ees_nt64_ENU.msi /qn APPDIR=C:\ESET\ ADDLOCAL=DocumentProtection
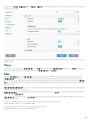
APPDATADIR=<path>
o
o
MODULEDIR=<path>
o
o

19
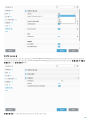
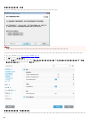
ADDLOCAL=<list>
o
o ESET .msi ees_nt64_ENU.msi /qn ADDLOCAL=<list>
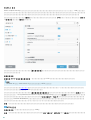
o ADDLOCAL http://msdn.microsoft.com/en-us/library/aa367536%28v=vs.85%
29.aspx
o ADDLOCAL
o ( )
o
o -
o -
o -
o -
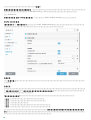
Endpoint 6.1
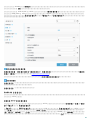
>
RealtimeProtection
>
>
DeviceControl
Web
WebAndEmail
Web
ProtocolFiltering
Web Web
WebAccessProtection
Web
EmailClientProtection
Web
MailPlugins
Web
Web Web
WebControl
UpdateMirror
Microsoft NAP
MicrosoftNAP
o WebAndEmail ProtocolFiltering
o EmailClientProtection MailPlugins
ees_nt64_ENU.msi /qn ADDLOCAL=WebAndEmail,WebAccessProtection,ProtocolFiltering
ees_nt64_ENU.msi /qn ADDLOCAL=WebAndEmail,EmailClientProtection,Antispam,MailPlugins
CFG
CFG_POTENTIALLYUNWANTED_ENABLED=1/0
0 - 1 -
PUA
CFG_LIVEGRID_ENABLED=1/0
0 - 1 -
LiveGrid
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
ページが読み込まれています...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
 91
91
-
 92
92
-
 93
93
-
 94
94
-
 95
95
-
 96
96
-
 97
97
-
 98
98
-
 99
99
-
 100
100
-
 101
101
-
 102
102
-
 103
103
-
 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
 109
109
-
 110
110
-
 111
111
-
 112
112
-
 113
113
-
 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
 135
135
-
 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
 142
142
-
 143
143
-
 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
-
 151
151
-
 152
152
-
 153
153
関連論文
-
ESET Internet Security ユーザーガイド
-
ESET SMART SECURITY ユーザーガイド
-
ESET Smart Security Premium ユーザーガイド
-
ESET Endpoint Antivirus ユーザーガイド
-
ESET Mail Security for Exchange Server ユーザーガイド
-
ESET Endpoint Antivirus ユーザーガイド
-
ESET Endpoint Security ユーザーガイド
-
ESET SMART SECURITY ユーザーガイド
-
ESET Endpoint Security ユーザーガイド
-
ESET Endpoint Antivirus ユーザーガイド



































































































































































